Recently “watering hole attacks” are getting popular among the hacking groups for targeting large groups of victims who routinely visit a popular website or discussion forum to share or discuss on common interests. Technically, these attacks work by tricking people to click on a “popular link” which is actually a window to download various malicious links/exploits on the victims’ machines.
This attack is analogous to the example of offering a child his favorite candy bar which is always “mouth watering” for them. Thus, the child almost always falls for this attack because that candy is his favorite. In the same way, if a group of people visit a popular “infected “website then it is easier to target the website itself to gather confidential data from large group of people rather than to target those people individually.
The rate of choosing and targeting specific users is very high here since different users might be using different browsers having different system configurations. After compromising the security of the website, the attacker posts a lucrative link on the website which attracts a lot of attention by the users. He then waits for some innocent user to visit that malicious link.
The malicious link obtains the data from the user browser to identify the details of system configuration. Accordingly, it then compares and downloads the relevant exploits silently to that system. This way each targeted user gets compromised. More number of users clicking on the link will provide for greater success of the attack.
Recently many websites were affected by these attacks including some prestigious ones, such as “Dalai Lama” website and US department of labor website etc. Conceptually speaking, this can also be considered as an alternate form of Spear Phishing attack.
How does the “watering hole attack” work?
For this attack, the attacker has to first identify the target group which visits a particular site frequently. The next step involves finding vulnerabilities in that particular website. Once the attacker ‘0wns’ (compromised) this website, it totally depends on his creativity and his intentions to collect valuable information about his victims and force feed malwares into their machines.
So for example, if the attacker wants to collect victim information, he would try to inject or load malicious JavaScript file/applet of his choice whenever the victim visits the website. The image shown below clarifies these steps in more detail.
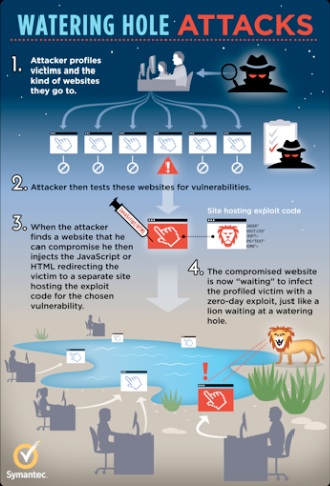
Image Source: http://www.symantec.com/connect/blogs/internet-explorer-zero-day-used-watering-hole-attack-qa
Now, the attacker will load malicious content in website by editing any of the main pages of the compromised website and tries to extract more information about the site members (or users) visiting it – such as browser version, OS details, Anti-virus installed etc. Accordingly, he can then determine which users are more prone to his exploits. With this information, he can accordingly send the exploits to chosen victims to easily compromise their machines.
Case Study of Dalai Lama website Attack
Let’s analyze recent attacks which happened on “Dalai Lama” website to understand this attack in practice. In this scenario, the attacker had compromised “http://tibet.net/” website and added some malicious code. This code redirected its visitors to xizang-zhiye(dot)org (this is the Chinese (CN) translated version of the site) which was vulnerable to Java exploit. This helped to install a backdoor as a payload.
It is to be noted that the English and other language versions except Chinese are not affected by this attack which again confirms he targeted nature of this attack. Presumably, the attack was sponsored by Chinese government to spy on its own people to monitor who were visiting the Tibetan site to show their support for Dalai Lama. For political reasons, Dalai Lama is not favoured by Chinese government and any support shown to him is not welcomed in China.
This threat actor has been quietly operating these sorts of watering hole attacks for at least a couple of years and also the standard spear phishing campaigns against a variety of targets that include Tibetan groups.
Technical Details of the attack
A 212kb jar file called YPVo.jar was downloaded on the victim’s machine which contained the Java exploit that is used to execute the backdoor. As per the Kaspersky Anti-virus scanner, the win32 executable file with size of 397KB named “aMCBlHPl.exe” was infected with Trojan Trojan.Win32.Swisyn.cyxf. This strongly suggests a targeted attack vector since previously also as per malware reported incidents; backdoors detected with the Swisyn frequently constitute as a part of APT related tool chains.
On further analysis, we find that this malicious code exploits 0-day vulnerability in Microsoft Internet Explorer called as ‘CDwnBindInfo’. Use-After-Free Remote Code Execution Vulnerability (CVE-2012-4792) is a 0-day vulnerability which affects Internet Explorer 8, Internet Explorer 7, and Internet Explorer 6.
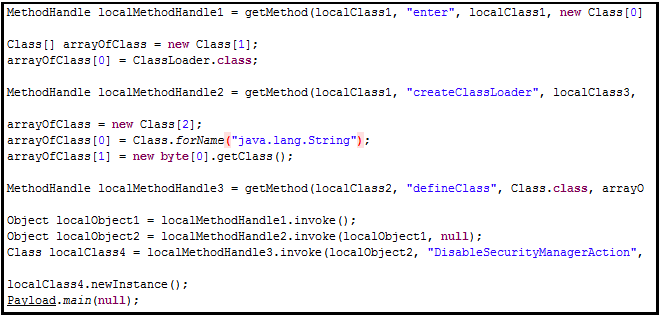
Source: http://www.securelist.com/en/blog/9144/Central_Tibetan_Administration_Website_Strategically_Compromised_as_Part_of_Watering_Hole_Attack
As it is evident from the code snippet shown above, the Java exploit makes use of the older CVE-2012-4681 vulnerability which was a popular Java 0Day submitted in August last year. The exploit has two classes Gondzz.class and Gondvv.class which disables the SecurityManager. The SecurityManager is responsible to protect the execution of unknown code directly into Java Virtual machine (JVM). With the SecurityManager being disabled, the payload is easily downloaded over a secure channel which is encrypted using AES and subsequently decrypted on the victim’s computer.
The payload contains a Windows32 executable which is executed but often detected by most of the anti-virus software such as Kaspersky. Hence, the attacker also needs to disable anti-virus solution from loading in start-up for carrying out a successful attack on victim machine. This information is available to him from the information gathering phase.
