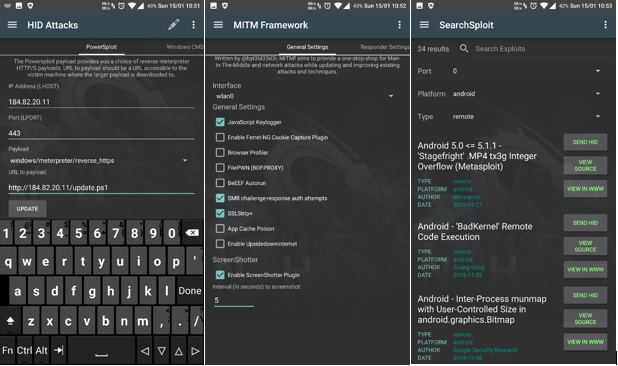
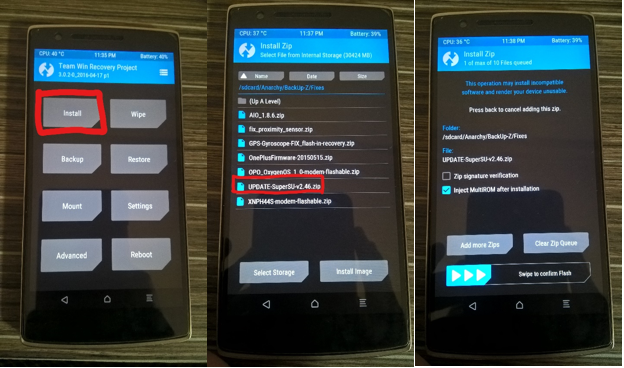
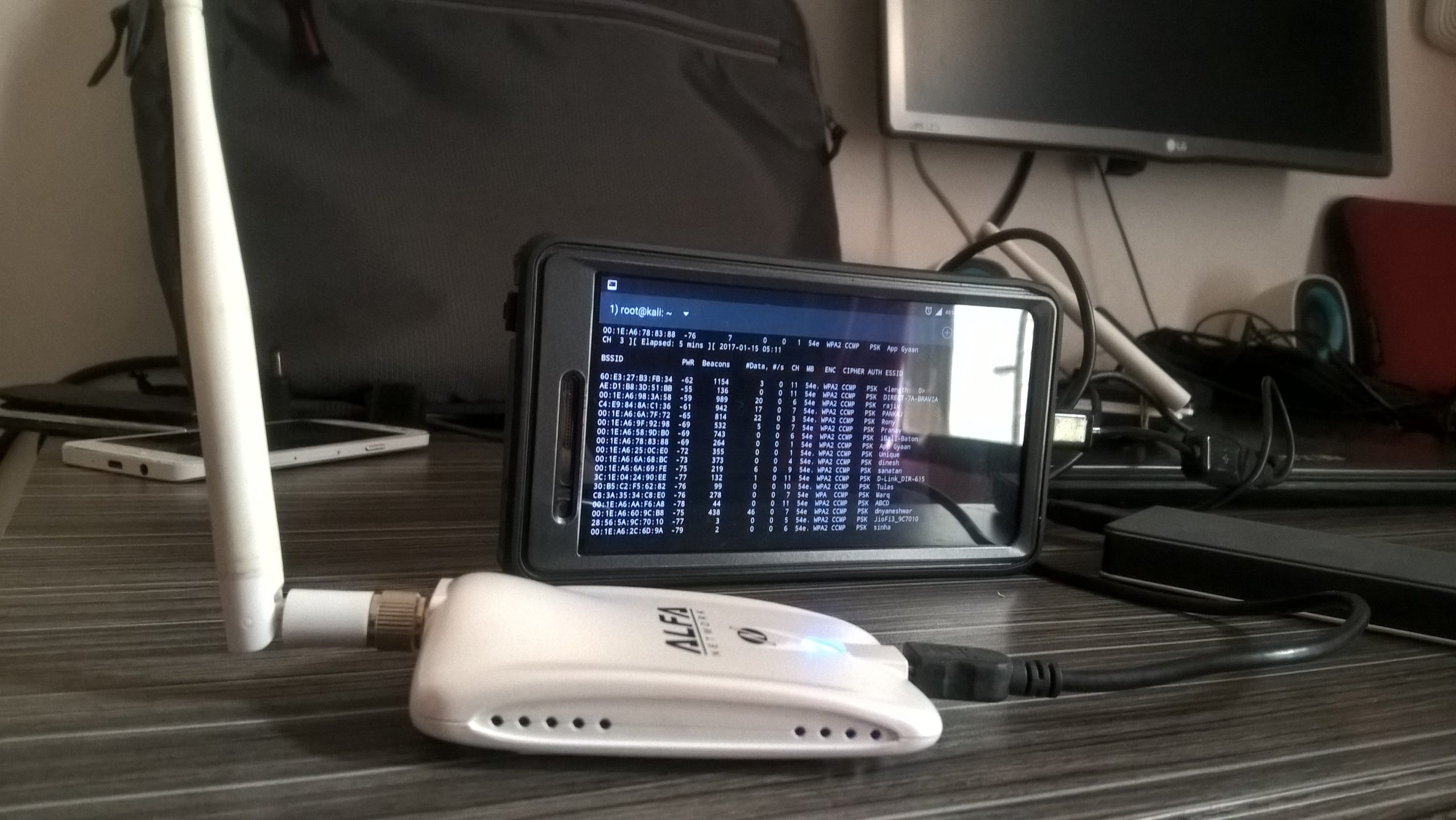
A Detailed Guide on OSCP Preparation – From Newbie to OSCP
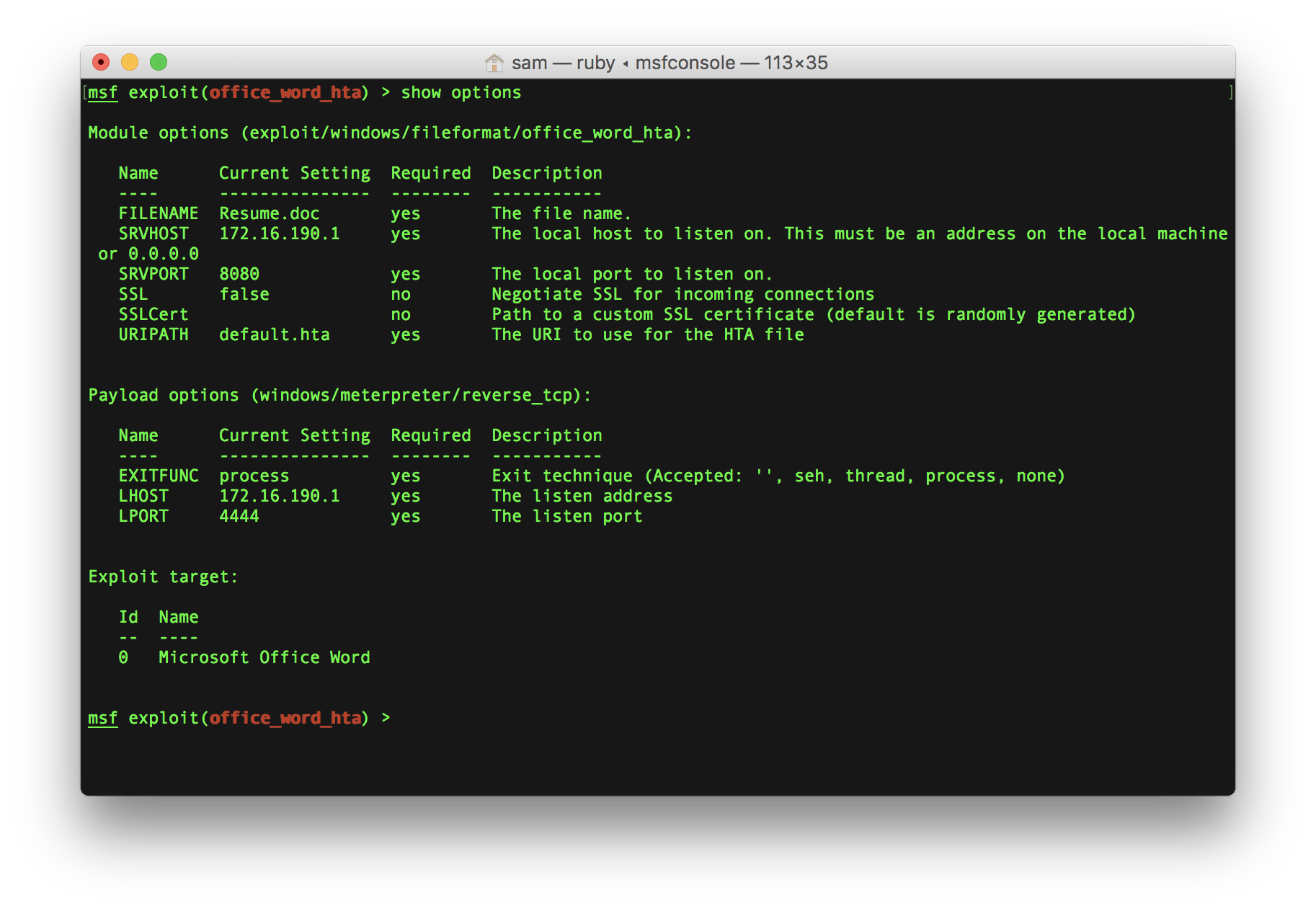
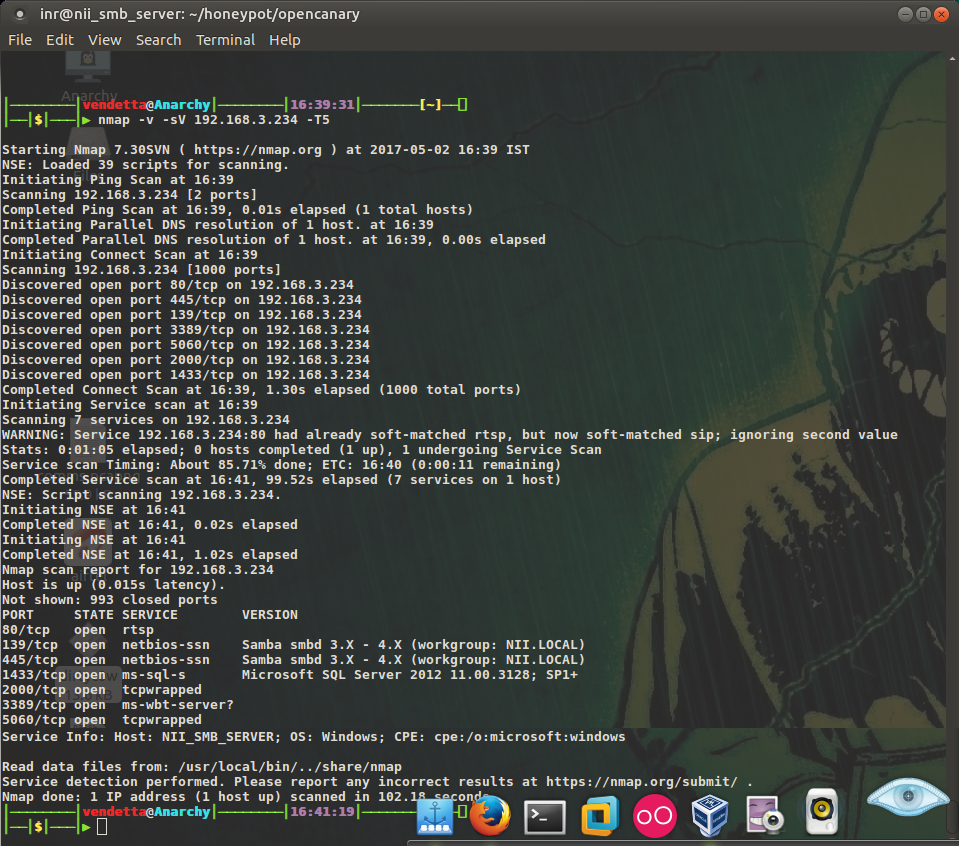
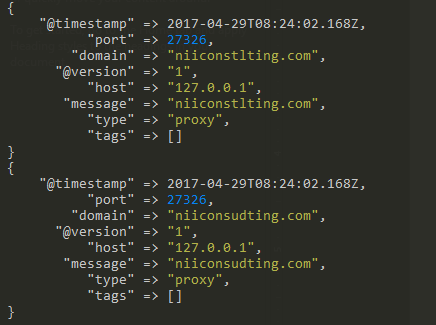
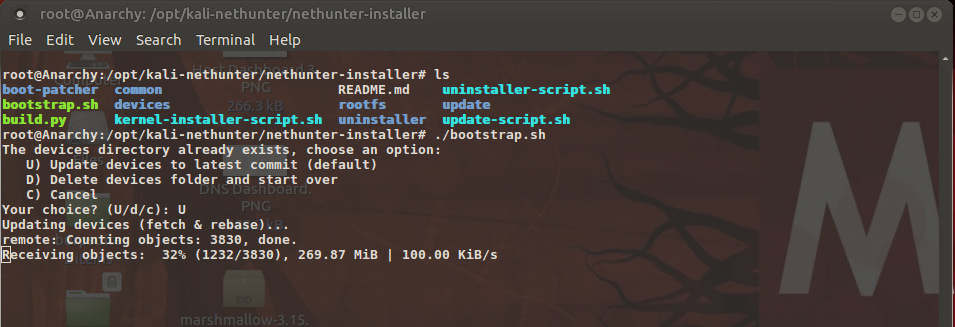
If you are a newbie in Penetration Testing and afraid of OSCP preparation, do not worry. Even I was once an amateur before starting on my OSCP journey. In this blog, I will provide you with a strategy for OSCP preparation. I will also share some resources that I found useful during my preparation. Here […]