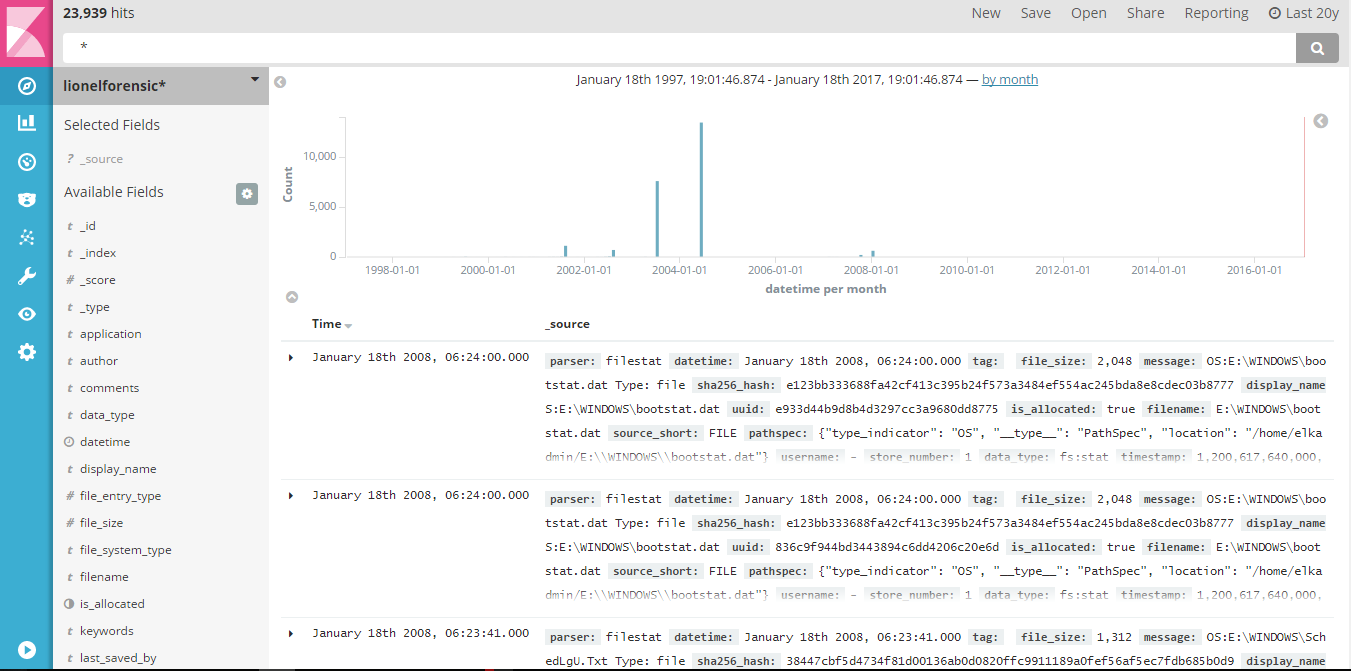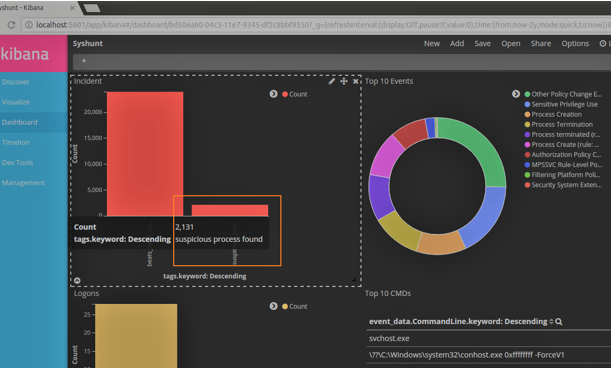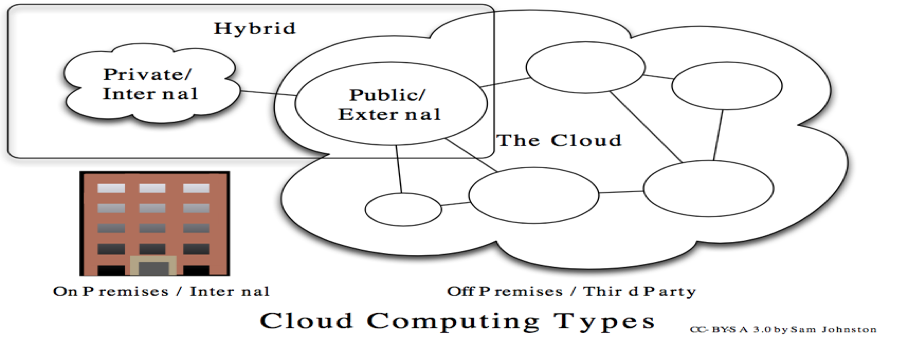
Security Analytics Using ELK
Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. Both sessions were great experiences and allowed me to see the growing interest among the information security folks for the opensource ELK stack. Those who know me personally or follow me on social media (Twitter/Linkedin) […]