Introduction
Cloud computing has redefined how businesses operate, offering unmatched agility, scalability, and cost-efficiency. But as enterprises migrate more workloads to the cloud, they encounter a crucial challenge: how to secure these workloads while maintaining flexibility.
According to Sprinter’s report, there has been a sharp rise in cloud-based cyberattacks, with data breaches, unauthorized intrusions, and crypto-mining exploits emerging as key threats.

Another report by Gartner predicts that Ninety percent of businesses will not regulate their use of public clouds and will inappropriately share sensitive information by 2025.
This demands more granular control, visibility, and segmentation within cloud architectures. Reactive defenses are no longer enough, security must be embedded into the very fabric of the cloud.
Whether it’s regulatory compliance, data privacy, or simply reducing the radius of cyber threats, network segmentation in the cloud is now a necessity.
However, building segmented environments in the cloud is not easy, especially across multi-cloud ecosystems. Major providers like AWS, Azure, and GCP don’t offer native, policy-driven tools to create isolated security domains.
This means enterprises are often left improvising security boundaries. To establish strong cloud infrastructure security, organizations must rethink segmentation strategies tailored to the cloud’s nature.
In this blog, you will get to know what all it requires for network segmentation in the cloud to enhance cloud security.
Understanding Micro-Segmentation in the Cloud
At the heart of modern cloud security lies a concept called micro-segmentation. It’s the practice of isolating different workloads or services, sometimes down to the process or container level to prevent unauthorized lateral movement.
Unlike traditional perimeter security, this approach operates on a much finer scale, where workloads, applications, and services each have defined access controls.
TL;DR: Micro-segmentation is about building small, secure zones within your cloud infrastructure to better control and monitor data flows and application behavior.
So, why does micro-segmentation matter in the cloud? Traditional security models simply don’t scale well here. In shared, dynamic cloud environments, the perimeter is blurry, and threats can spread fast.
Without clear internal boundaries, a single compromised workload can compromise the whole environment. That’s why micro-segmentation becomes an integral pillar of cloud infrastructure security.
What is Cloud Network Segmentation?
In simple terms, cloud network segmentation is the act of dividing your cloud infrastructure into isolated zones or segments. These zones are based on roles, risk levels, compliance mandates, or business functions. You can then apply specific access controls to govern communication between segments.
Because cloud network segmentation adds layer after layer of security to IT systems and data, it can effectively lower the risk of data breaches.
This multi-layered cybersecurity approach stops dangerous viruses from propagating throughout all of a company’s networks. Additionally, it can effectively prevent hackers from swiftly breaking into networks and remove the chance that private information would be compromised.
Benefits of Cloud Network Segmentation
Cloud network segmentation helps reduce attack surfaces by limiting communication paths between workloads.
It improves visibility, strengthens compliance posture, and allows security teams to control traffic based on business policies.
With segmentation, organizations gain tighter control over east-west traffic, making it harder for attackers to move laterally within the network. Ultimately, this enhances cloud infrastructure security while keeping cloud operations agile.
Cloud network segmentation enables organizations to reduce cyber risk by logically isolating workloads and applications within cloud environments. This improves traffic control, limits exposure to lateral movement in case of a breach and enables security policies to be tightly aligned with business functions.
For example, in BFSI, customer-facing apps (like mobile banking) can be segmented from internal payment processing systems, ensuring tighter compliance with PCI DSS and minimizing risk exposure. Segmentation also simplifies regulatory audits by clearly defining security zones for regulated data.
How Segmentation Helps
Segmentation prevents attackers from moving laterally across the cloud environment if a single system is compromised.
For example, if a malicious actor exploits a vulnerability in a web application in a retail bank, micro-segmentation ensures that sensitive systems like core banking platforms remain unreachable, effectively containing the threat within its origin zone.
1. Enables Granular Policy Enforcement
Cloud network segmentation allows organizations to apply precise access policies at workload or even process level.
For instance, in insurance companies, customer claim management tools can be segmented from actuarial data systems, with role-based controls defining exactly who or what can access specific datasets or services. This ensures operational integrity while reducing insider risks.
2. Supports Compliance and Data Governance
Regulations such as PCI DSS, etc., cybersecurity guidelines require strict controls over data flow. Segmentation helps meet these by clearly demarcating data domains and applying controls specific to regulatory scope.
In BFSI, this means storing and processing credit card data within isolated, audited network segments and restricting access based on regulatory zones.
3. Enhances Incident Containment and Response
When breaches happen, segmentation limits the attack radius, making it easier for security teams to isolate compromised segments and prevent further spread.
For example, if a misconfigured API in an investment platform is exploited, segmentation helps quickly cut off communication between the breached service and backend databases holding client financial records, minimizing potential damage.
Key Requirements for Cloud Network Segmentation
To get segmentation right in a cloud-native world, enterprises need to rethink traditional approaches and embrace cloud-specific techniques.
1. Adopt that Cloud is Agile: First, accept that cloud environments are highly dynamic. IPs change, workloads scale up and down, and infrastructure evolves daily.
This demands a flexible change management process where segmentation rules are not static but dynamically applied, preferably through tags, labels, and automation.
2. Extending Traditional Security Controls into Virtual Environments: BFSI firms often operate hybrid setups. Legacy data centers with firewalls and VLANs must logically extend segmentation policies into the cloud.
This means replicating those controls using cloud-native tools (e.g., AWS Security Groups, Azure NSGs) or overlays. A fraud detection engine hosted on-prem can still enforce consistent rules when interacting with cloud-based analytics tools.
3. Embedding Security into Application Development: DevSecOps must be aligned with segmentation policies. Developers should know where their apps sit in the security architecture.
For example, during app development for a mortgage approval workflow, developers should tag services that handle sensitive PII to auto-segment those workloads under stricter policies. Educating teams ensures segmentation is not an afterthought but part of the building process.
4. Use of Cloud-Ready Firewalls for Fine-Grained Traffic Control: Cloud-native firewalls (e.g., Azure Firewall, AWS Gateway Firewall) and third-party solutions (e.g., Palo Alto) support application-aware filtering and DPI.
These tools are vital in BFSI for scenarios like monitoring traffic from a third-party fintech integration to the internal settlement system, ensuring no unauthorized protocol or suspicious payload gets through.
Best Practices for Cloud Network Segmentation
Let’s break down the best practices that enterprises can adopt to make segmentation successful in the cloud:
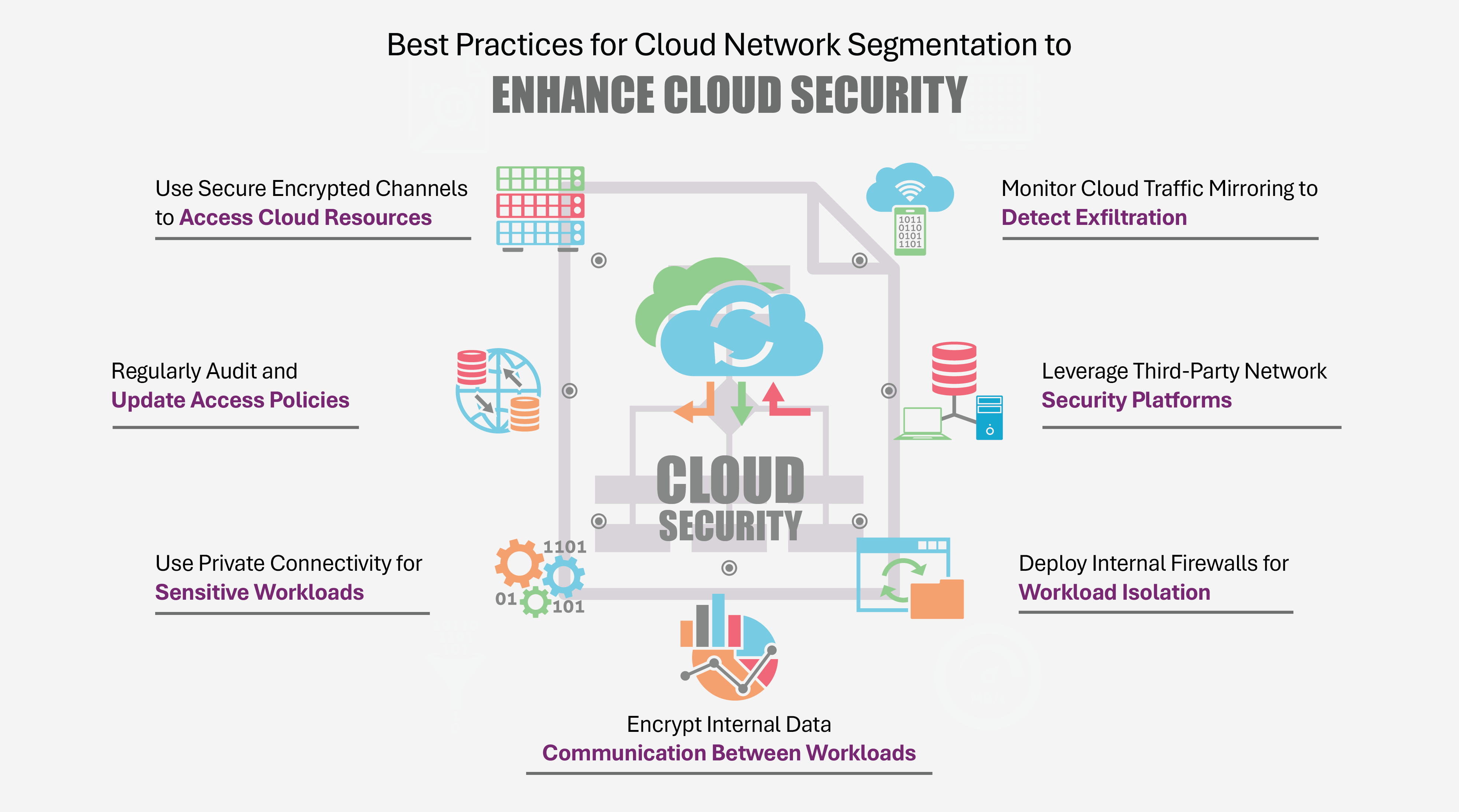
1. Use Secure Encrypted Channels to Access Cloud Resources
Every connection, especially to management consoles, databases, or APIs should be encrypted using protocols like TLS 1.3.
For example, a credit underwriting platform accessed by remote employees should use VPN-over-SSL or SASE solutions to ensure encrypted, authenticated entry, minimizing the attack surface exposed to the internet.
2. Regularly Audit and Update Access Policies
Access policies must evolve with workloads. A monthly audit cycle can identify misaligned permissions, unused rules, or privilege creep.
In BFSI, this could mean revisiting segmentation rules for apps accessing core banking APIs during quarterly compliance reviews, ensuring only relevant microservices retain access and outdated ones are decommissioned.
3. Use Private Connectivity for Sensitive Workloads
When handling sensitive workloads like payment processing, use private connectivity options like AWS Direct Connect, Azure ExpressRoute, or Google Cloud Interconnect.
These bypass the public internet, reducing exposure. BFSI enterprises can use such channels for secure data syncs between their on-prem fraud detection systems and cloud AI models.
4. Encrypt Internal Data Communication Between Workloads
Even east-west traffic within cloud environments should be encrypted. Attackers can sniff unencrypted traffic if they breach a zone.
For instance, ensure encryption between a front-end trading platform and the backend order matching engine within a brokerage firm’s cloud stack to mitigate sniffing and man-in-the-middle risks.
5. Deploy Internal Firewalls for Workload Isolation
Micro-firewalls between cloud compute instances enforce “least privilege” communication. For example, ensure that a CRM system in a bank cannot talk to the core ledger system directly unless explicitly permitted.
This ensures that even if one segment is exploited (e.g., via phishing), critical backend systems remain protected.
6. Monitor Cloud Traffic Mirroring to Detect Exfiltration
Cloud providers offer traffic mirroring for debugging, but attackers can abuse this to siphon data. Implement monitoring solutions to track and alert any unexpected mirroring configurations.
7. Leverage Third-Party Network Security Platforms
Advanced platforms like Zscaler, Prisma Cloud, or Fortinet CNAPPs provide deep visibility across cloud workloads and enforce segmentation with unified policies across clouds.
BFSI institutions with global branches can benefit by deploying consistent segmentation and DLP policies across multiple cloud accounts from a single pane of glass, improving governance and response.
These practices not only enhance cloud infrastructure security but also help organizations remain agile and compliant.
Segmentation for Cloud Maturity: From Control to Confidence
Cloud environments are dynamic, scalable, and transformative but they come with new risks that demand new security models. Network segmentation is one such model that empowers enterprises to limit attack surfaces, contain threats, and meet compliance with confidence.
As we have seen, segmentation isn’t just about drawing boundaries, it’s about defining relationships between workloads and governing them wisely. It’s an ongoing discipline that adapts as your cloud grows.
With a thoughtful mix of cloud-native capabilities and third-party integrations, organizations can build robust segmentation strategies that scale. The end goal? A resilient cloud that enables innovation while protecting what matters most.
By mastering network segmentation, you are not just ticking a security box, you are laying the foundation for a truly secure cloud infrastructure. And that’s a strategy worth investing in.
We help enterprises implement granular segmentation, enforce zero trust, and gain real-time visibility across multi-cloud environments.
Our cloud security services are built to combat today’s threats- ransomware and lateral movement, with policy automation and AI-driven threat detection. Let’s build a cloud that’s not just scalable, but truly secure.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
