Just a month after January’s Fortinet breach, where 15,000 organizations’ FortiGate firewall data were leaked by threat actor, Belson Group, another critical vulnerability has emerged. Fortinet has sounded the alarm on yet another high-stakes cyber threat- a zero-day authentication bypass vulnerability, CVE-2025-24472 (CVSS 8.1), actively exploited by attackers.
The vulnerability resides in both FortiOS and FortiProxy, giving threat actors a dangerous opportunity to hijack Fortinet firewalls and infiltrate networks undetected
Hackers’ Shortcut to Admin Control
This vulnerability means a remote attacker can use a special technique to bypass security checks and take control of the system.
They could do this by sending crafted requests to certain parts of the system, such as the Node.js web socket module or the CSF proxy, essentially finding a backdoor to sneak in.
This vulnerability is a master key handed straight to attackers, and here’s what they can do:
· Hackers can slip past authentication and gain super-admin privileges.
· Create fake admin accounts, rewrite firewall rules, and quietly slide into SSL VPN user groups.
· Move through internal systems undetected, exfiltrating data or launching deeper attacks.
It’s like hostile takeover of your security defenses, where the intruders seize control. And unless patched immediately, this flaw leaves the door wide open.
Fortinet’s FortiOS, the core operating system running on FortiGate firewalls, has faced repeated security flaws over the years. These zero-day vulnerabilities have become a recurring target for hackers.
The latest vulnerability, CVE-2025-24472, is just another addition to a long list of security issues that have plagued FortiOS.
Each new vulnerability is not just a flaw, it’s an opportunity for cybercriminals to infiltrate critical networks.
Shared Vulnerabilities Across Major Players
It’s worth noting that Fortinet isn’t the only player facing these challenges. Industry giants like Palo Alto Networks and Cisco have experienced their share of security flaws, showing that no organization is immune to these threats.
· In November 2024, Palo Alto Networks faced a serious security crisis when two major vulnerabilities, CVE-2024-9474 and CVE-2024-0012, were discovered in its firewalls.
Attackers could first bypass authentication, gain unauthorized access to the firewall, and then manipulate security policies. Many organizations relying on Palo Alto’s firewalls were exposed, highlighting yet another major security lapse in enterprise cybersecurity.
· Similar incidents were also seen in Cisco’s CLI. In July 2024, a critical vulnerability in Cisco NX-OS Software, CVE-2024-20399, was exploited by a China-linked threat group to hijack Cisco switches.
The flaw allowed attackers with administrator credentials to plant custom malware, steal sensitive data, and maintain persistent access to corporate networks. · In 2023, a critical VMware ESXi vulnerability (CVE-2023-20867) was exploited, allowing attackers with root access to bypass authentication in VMware Tools and compromise system integrity.
Cybercriminals are no longer just opportunistic hackers; they are calculated, relentless, and always a step ahead.
The Persistent Threat Against Fortinet
Attackers have leveraged everything from authentication bypasses to remote code execution to gain unauthorized access and escalate privileges rapidly.
This ongoing pattern of exploitation raises a critical question- what trends can we identify over time?
To gain deeper insights, we leveraged our AI-powered cloud platform, Transilience AI, to analyze Fortinet’s historical vulnerabilities in its impact on FortiOS and FortiProxy.
The platform provided a comprehensive view of severity scores, version of product affected, and more, helping us uncover key security gaps and emerging risks.
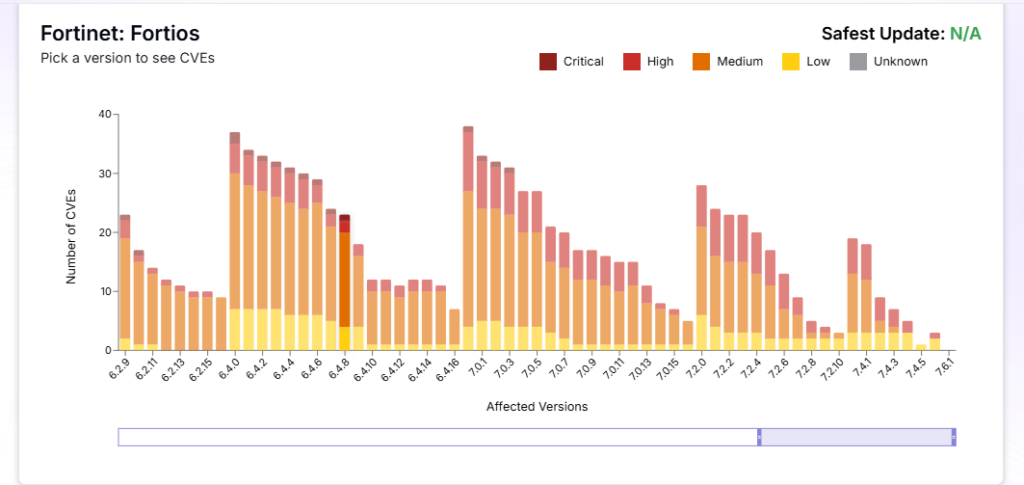
Source: Transilience.ai
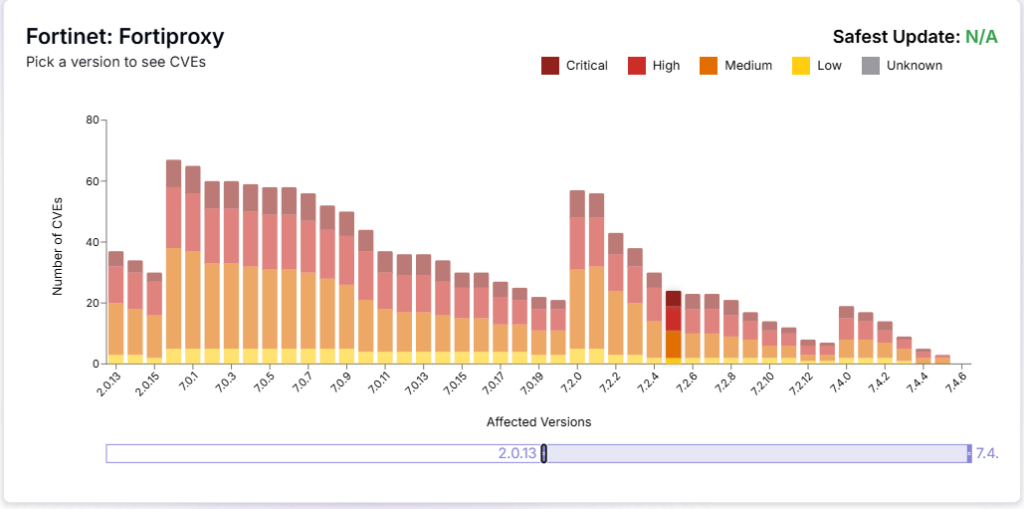
Source: Transilience.ai
Here’s a look at other critical Fortinet vulnerabilities in recent years:
· CVE-2024-21762: A memory corruption issue (out-of-bounds write) that lets attackers execute malicious code remotely.
· CVE-2024-46666: Device DoS via APREQ library errors in the way files are uploaded.
· CVE-2023-27997: A buffer overflow vulnerability that could enable remote code execution, giving hackers full control over the device.
| S.No | Vulnerability | Products Impacted | Product Versions |
| 1 | CVE-2024-21762 | FortiOS and FortiProxy | FortiOS 7.4, 7.2, 7.0, 6.4, 6.2, 6.0, FortiProxy 7.4, 7.2, 7.0, 2.0, 1.2, 1.1, 1.0 |
| 2 | CVE-2024-46666 | FortiOS VPN | FortiOS 7.6.0, 7.4.4, and more |
| 3 | CVE-2023-27997 | FortiOS (FortiGate Firewalls) | FortiOS 7.2.4, 7.0.11, 6.4.12, and more |
The Wave of Attacks on Fortinet Products
For years, Fortinet products have been prime targets for cyberattacks, with critical vulnerabilities repeatedly exploited in the wild. Attackers have used these flaws to bypass security controls, infiltrate networks, and gain unauthorized access to sensitive systems.
Here are some of them which have been actively exploited by attackers, leading to security breaches:
· CVE-2022-40684: In January 2025, a dark web leak exposed 15,000 FortiGate firewall credentials dating back to 2022, a breach tied to earlier issues like CVE-2022-40684.
Even though the leaked data isn’t new, it underscores how persistent and determined advanced threat actors are in targeting Fortinet devices. · CVE-2024-55591: An authentication bypass flaw known as CVE-2024-55591 gave attackers super-admin access to FortiOS and FortiProxy.
· Since November 2024, this vulnerability has been actively used.
· To obtain access, attackers sent specially constructed requests to the Node.js web socket module.
· Approx 48,000 internet-facing devices worldwide were affected by this vulnerability.
These incidents serve as a reminder that vulnerabilities, no matter how old, can be exploited if left unaddressed, making ongoing vigilance and prompt patching essential for maintaining strong network security.
Immediate Countermeasures for Asset Owners and Admins
As cyber threats evolve, the urgency to act swiftly and effectively cannot be overstated. With continuous attacks targeting firewall vulnerabilities, asset owners and firewall administrators must take every precaution to safeguard their systems.
Here are some steps to secure Fortinet devices and mitigate potential damage:
1. Patch Immediately: Update your Fortinet devices to the latest firmware as soon as possible.
In some cases, patching alone may not fully address the issue, as attackers can exploit known vulnerabilities before patches are applied, leaving systems exposed. Hence, administrators should restrict access to vulnerable systems by using IP whitelisting and enforcing multi-factor authentication on critical accounts to mitigate unauthorized access.
2. Secure Management Access: Limit access to management interfaces, ensuring they are only available on trusted networks and not open to the public.
3. Monitor Logs: Regularly review system logs for unusual activities like unexpected admin account creations or changes in SSL VPN settings.
4. Enable MFA: Use multi-factor authentication on administrative accounts to add an extra layer of security.
5. Apply Workarounds: Consider disabling the HTTP/HTTPS admin interface or restricting access.
Vulnerabilities are exploited faster than they can be patched, putting networks at constant risk. A well-maintained defense system helps anticipate challenges before they escalate.
Cybersecurity Never Sleeps: Prepare for the Next Wave
Over the years, vulnerabilities in Fortinet products have been exploited, exposing enterprises that use these products to severe risks.
This certainly won’t be the last critical Fortinet vulnerability we see in 2025; more are bound to surface as threat actors refine their tactics.
The continuous targeting highlights a larger trend of persistent vulnerabilities in security products, reminding organizations that patching alone isn’t enough.
As cybercriminals grow more sophisticated, leveraging AI-driven security solutions can help detect and prioritize vulnerabilities faster, strengthening overall resilience. Our AI-powered platform, Transilience AI, empowers security teams with automated threat detection and intelligent vulnerability prioritization and helps them assess critical CVEs and more, enabling faster response times and reducing attack exposure.
With contextual security insights and AI-powered automation, organizations can move beyond reactive defense and build a future-ready cybersecurity strategy.
To learn how Transilience AI enhances threat intelligence and streamlines security operations, explore our solutions or connect with our experts for deeper insights.

