How Real-Time Intelligence is Shaping Defense Strategies
The cybersecurity landscape in 2025 continues to be shaped by an increasingly sophisticated threat ecosystem. Cybercriminals are leveraging advanced techniques, including AI-driven attacks, vulnerability exploits, and Ransomware-as-a-Service (RaaS), to orchestrate large-scale cyber incidents.
Traditional reactive security measures are proving insufficient, making real-time cyber threat intelligence essential for identifying and mitigating emerging threats before they cause significant damage.
A report by Slashnext reveals that between 2023 and 2024, there has been an increase in credential phishing by 217%. This means that attackers are refining their techniques to deceive users into revealing sensitive information.
Modern cyber threats extend beyond conventional malware. Trojans, AI-powered phishing, and automation-driven cyberattacks have drastically increased, forcing organizations to rethink their defensive strategies. To stay ahead, security teams must adopt adaptive intelligence, real-time exploit tracking, and collaborative threat-sharing models to bolster their cyber resilience
Fighting Malicious Threats with Cyber Threat Intelligence
1. Trojans or Malicious Software
Trojans have become a lucrative tool for cybercriminals, enabling unauthorized access to sensitive systems. The sale of compromised credentials on the dark web fuels further cyberattacks, from business email compromise (BEC) to ransomware infiltration.
In 2024 alone, 2.1 billion credentials were stolen by infostealer attacks, highlighting the alarming scale of this threat
By analyzing threat intelligence data, security teams can identify indicators of compromise, track adversary behavior, and proactively defend against emerging threats.
Real-World Cases of Trojan Attacks: Malware families such as Vidar, Redline, Racoon, and Risepro continue to evolve, bypassing traditional security measures.
Threat actors use this malicious software to harvest credentials, which are then exploited to infiltrate corporate environments. The low cost and widespread availability of these tools pose a growing challenge for security teams
Defense Strategies
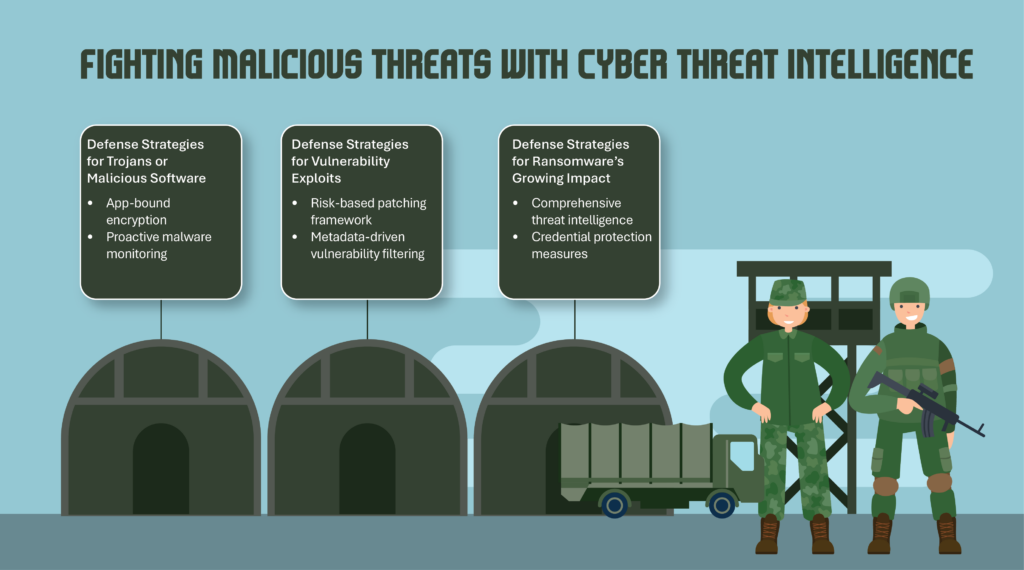
- App-bound encryption: The latest encryption mechanisms prevent unauthorized applications from accessing sensitive credential data.
- Proactive malware monitoring : Tracking emerging malware strains helps organizations respond swiftly to new threats.
2. Vulnerability Exploits
Organizations face an overwhelming number of vulnerabilities, with over 30% of reported flaws categorized as high or critical in 2024.
- Traditional risk assessment models, such as CVSS, often fail to provide actionable intelligence, leaving security teams struggling to determine which vulnerabilities demand immediate attention.
- Attackers capitalize on organizations’ delayed patching strategies, often targeting zero-day vulnerabilities or less-publicized flaws. This reactive approach results in prolonged exposure, increasing the risk of breaches.
Real-time exploit intelligence allows organizations to focus on vulnerabilities that are actively being weaponized, reducing unnecessary patching workloads and improving overall security posture.
Defense Strategies
- Risk-based patching framework: Organizations should prioritize patching vulnerabilities based on exploitability rather than severity scores alone.
- Metadata-driven vulnerability filtering: Leveraging exploit intelligence can help security teams cut critical vulnerability workloads by over 80%, improving efficiency and effectiveness.
3. Ransomware’s Growing Impact
By 2031, ransomware attacks would happen every two seconds, or 43,200 attacks every day, according to Norton’s estimate.
It’s predicted that ransomware would have caused $265 billion in measurable losses worldwide.
- The rapid evolution of Ransomware-as-a-Service (RaaS) and the integration of AI-powered attack automation have made ransomware campaigns more effective and widespread.
- Ransomware operators now offer subscription-based services, significantly lowering the barrier to entry for cybercriminals. The commoditization of ransomware enables even low-skill threat actors to execute devastating attacks.
- Threat actors increasingly rely on AI to craft sophisticated phishing lures, automate credential harvesting, and streamline ransomware deployment.
Defense Strategies
- Comprehensive threat intelligence: Organizations must integrate real-time intelligence feeds to predict and mitigate ransomware threats.
- Credential protection measures: Implementing MFA and credential-hardening techniques can significantly reduce attack surfaces.
The Future of CTI: Next Steps
Static security models are no longer effective in the face of dynamic cyber threats. Organizations must embrace adaptive threat intelligence to anticipate and counteract evolving attack techniques.
1. AI-Powered Threat Detection and Behavioral Analytics
Machine learning-driven analytics enable faster detection of anomalies, helping security teams identify threats before they escalate into major breaches.
2. Collaboration Between Security Teams and Threat Intelligence Providers
Cyber defense is no longer an isolated effort. Organizations must collaborate with industry peers, intelligence-sharing networks, and third-party security providers to strengthen their security posture.
3. Continuous Defense Adaptation
Threat intelligence should not be a one-time initiative. Continuous monitoring, risk assessment, and real-time data correlation are crucial for maintaining resilience against emerging threats.
The Next Frontier in Defense is Dynamic Intelligence
As cyber threats grow more sophisticated, organizations must shift from reactive defense strategies to proactive intelligence-driven security models.
The integration of AI, behavioral analytics, and real-time exploit intelligence will be instrumental in countering emerging threats in 2025 and beyond.
By prioritizing adaptive threat intelligence, security teams can stay ahead of adversaries, mitigating risks before they materialize into full-scale attacks.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
