Evolving Landscape of Cloud Infrastructure Security
Businesses are rapidly migrating to the cloud, drawn by its scalability and efficiency. However, this transition brings forth complex security challenges that demand a fresh perspective.
According to Market Research Future, the CNAPP market is projected to grow from USD 10.74 billion in 2025 to USD 59.88 billion by 2034, highlighting the escalating need for robust cloud security solutions.
While CNAPPs aim to provide comprehensive protection, they sometimes fall short, particularly in delivering real-time detection and response capabilities. This often results in an overwhelming issue, leaving organizations uncertain about where to focus their remediation efforts for maximum impact.
Understanding the Challenges in Cloud Infrastructure Security
1. Cloud Misconfigurations: The Silent Culprits
Cloud misconfigurations have emerged as a leading cause of data breaches. Simple oversights such as unrestricted inbound ports, disabled logging, exposed access keys, and overly permissive account permissions can inadvertently open doors to malicious actors.
2. The Rise of Sophisticated Adversaries
Modern threat actors are no longer solely motivated by financial gain or intellectual property theft.
- The democratization of phishing kits and hacking tools, along with the rise of Cybercrime-as-a-Service, has lowered the barrier to entry for cybercriminals.
- Automated tools enable attackers to scan for vulnerabilities, perform brute-force attacks, and execute malicious activities at an unprecedented pace, outstripping traditional manual methods.
This is where CNAPP, or Cloud-Native Application Protection Platform, comes into play. CNAPP is a unified security framework designed to protect cloud-native applications across their entire lifecycle, from development and deployment to runtime.
Instead of relying on fragmented tools for workload protection, vulnerability scanning, compliance, and access control, CNAPP aims to bring all of these under one roof. It’s essentially a full-stack security suite tailored for the complexity of modern cloud environments.
Let’s take an example of BFSI, where CNAPP offers a strong foundation for visibility and prioritization. But as threats become more identity-driven and span across multiple cloud platforms, organizations must augment CNAPP with intelligent, real-time detection frameworks that break down security silos and respond to threats as they happen.
Recognizing the Limitations of CNAPP
While CNAPPs offer a broad range of security features, they are not without their limitations:
- Blind Spots in On-Premises Workloads: CNAPPs primarily focus on cloud environments, often neglecting on-premises workloads, which can lead to security gaps.
- Detecting Cross-Domain Threats: The siloed nature of many CNAPPs can hinder the detection and mitigation of threats that span multiple domains, such as cloud and on-premises systems.
- Security Silos Due to Vendor Lock-In: Relying on a single vendor for CNAPP solutions can result in security silos, limiting integration capabilities with other security tools and reducing overall visibility.
- Risks from Third-Party Integrations: Integrating third-party applications can introduce vulnerabilities if not properly vetted, posing additional security challenges.
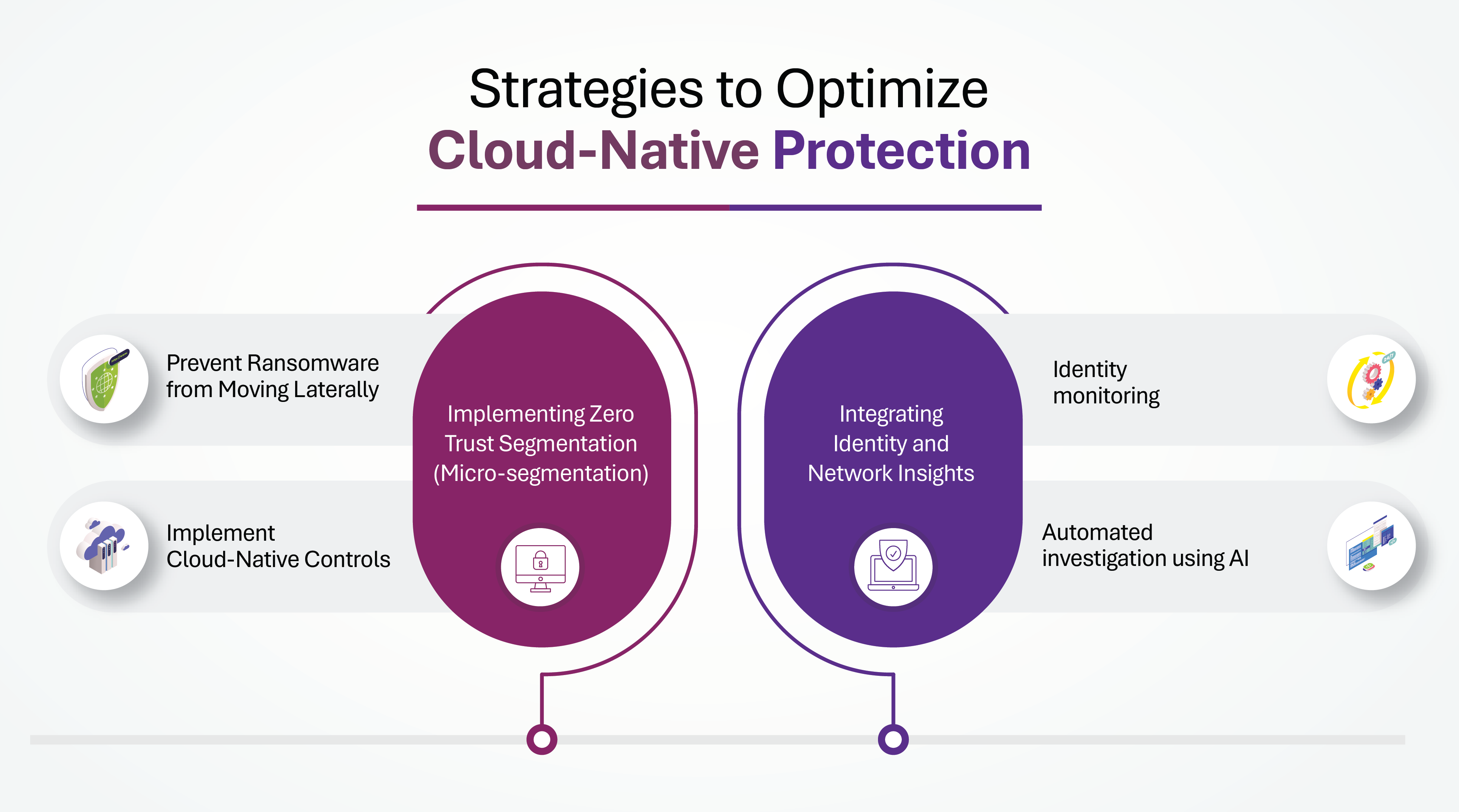
Strategies to Overcome CNAPP Challenges
Integrating Identity and Network Insights
Today, the cloud is dynamic, hybrid, and heavily identity driven. This means that identities (both human and machine) are the new perimeter.
At the same time, the network layer still plays a critical role in how workloads communicate. But here’s the problem- too many organizations look at these elements, identity, network, runtime activity, in isolation.
What’s needed is a holistic lens that blends identity context with network and cloud runtime activity to detect and stop threats that cross traditional security boundaries.
Imagine the cloud environment of a BFSI organization which has hundreds of microservices deployed across AWS and Azure. An attacker compromises a developer’s access key.
A. Identity Monitoring: If the security team is only monitoring network behavior, they might miss that this identity is suddenly accessing storage buckets. But with identity monitoring in place, especially one powered by CNAPP with AI-driven context, the system can detect this anomaly in real time and alert the SOC instantly.
If identity, network, and cloud runtime data are unified, backed by AI that prioritizes the alert based on impact, the SOC team can respond with precision.
B. Automated Investigation Using AI: With automated investigation using AI, we can flag the event, suggest root cause, and even recommend remediation steps.
This level of context-rich, real-time monitoring is what makes modern cloud security adaptive, not just reactive.
2. Implementing Zero Trust Segmentation (Micro-segmentation)
Traditional firewalls can’t keep up with the dynamic nature of cloud-native apps, containers, and APIs.
Zero Trust segmentation or micro-segmentation helps contain the damage by limiting how far an attacker can move if they get in.
Even if an attacker gets in, they can’t move laterally to compromise more assets. It’s like building fire doors into your cloud environment that close automatically the moment smoke is detected.
A. Prevent Ransomware from Moving Laterally: Zero Trust Segmentation is implemented by logically grouping users, devices, and workloads based on identity, context, and behavior, not just IP addresses or locations.
Since everything is software-defined and automated, segmentation that took months using legacy firewalls or network switches can be done in days using APIs and infrastructure-as-code (IaC). This will reduce the attack surface and lateral movement risk.
B. Implement Cloud-Native Controls: With Zero Trust in the cloud, you don’t need all that expensive hardware anymore. Instead, security is built directly into the cloud using identity-based access, software-defined segmentation, and cloud-native controls.
This results in simpler architecture, faster performance, and up to 50% lower costs on security infrastructure.
Beyond the technical advantage, micro-segmentation also aligns perfectly with today’s multi-cloud reality.
Whether you are running workloads across AWS, Azure, and Google Cloud, or a hybrid setup involving on-prem systems, this segmentation ensures that consistent policies can be applied.
You gain real-time visibility, policy control, and the ability to plug in third-party tools without creating additional attack surfaces.
Zero Trust is a measurable way to shrink your attack surface, control privilege creep, and enforce least privilege access at every level of your cloud infrastructure.
By segmenting the network into smaller, isolated segments, organizations can effectively contain breaches and prevent lateral movement within the network.
Embracing a Holistic Approach to Cloud Security
The dynamic nature of modern cloud infrastructures necessitates a shift from traditional, fragmented security tools to integrated solutions that offer comprehensive visibility and control.
By combining the capabilities of CNAPPs with AI-driven, identity-aware, cross-domain detection frameworks, organizations can proactively address emerging threats and build a resilient cloud security posture.
As cloud environments continue to grow in complexity, intelligence and integration will be the cornerstones of effective cloud infrastructure security.
Ready to move beyond fragmented cloud visibility? Our advanced Network Intelligence capabilities bring deep context to your cloud infrastructure security, combining identity, behavior, and traffic patterns for smarter detection and response.
We help you pinpoint real threats across environments, not just scan for surface-level issues. Let’s talk about securing your cloud with precision, not just protection.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
