Quest for Healthcare Compliance Relies on a Unified Security Approach
As digital transformation picks up speed, the amount of sensitive patient information being created and stored is growing rapidly. But many healthcare organizations are struggling to keep up with security measures and compliance requirements due to outdated IT systems, lack of skilled staff, and other obstacles. The consequences? Think fines, loss of patient trust, and disruptions in day-to-day operations.
According to a survey conducted by Omdia and Coalfire on the subject matter experts in the healthcare, educational, and financial sectors, they encounter specific difficulties when it comes to managing compliance.
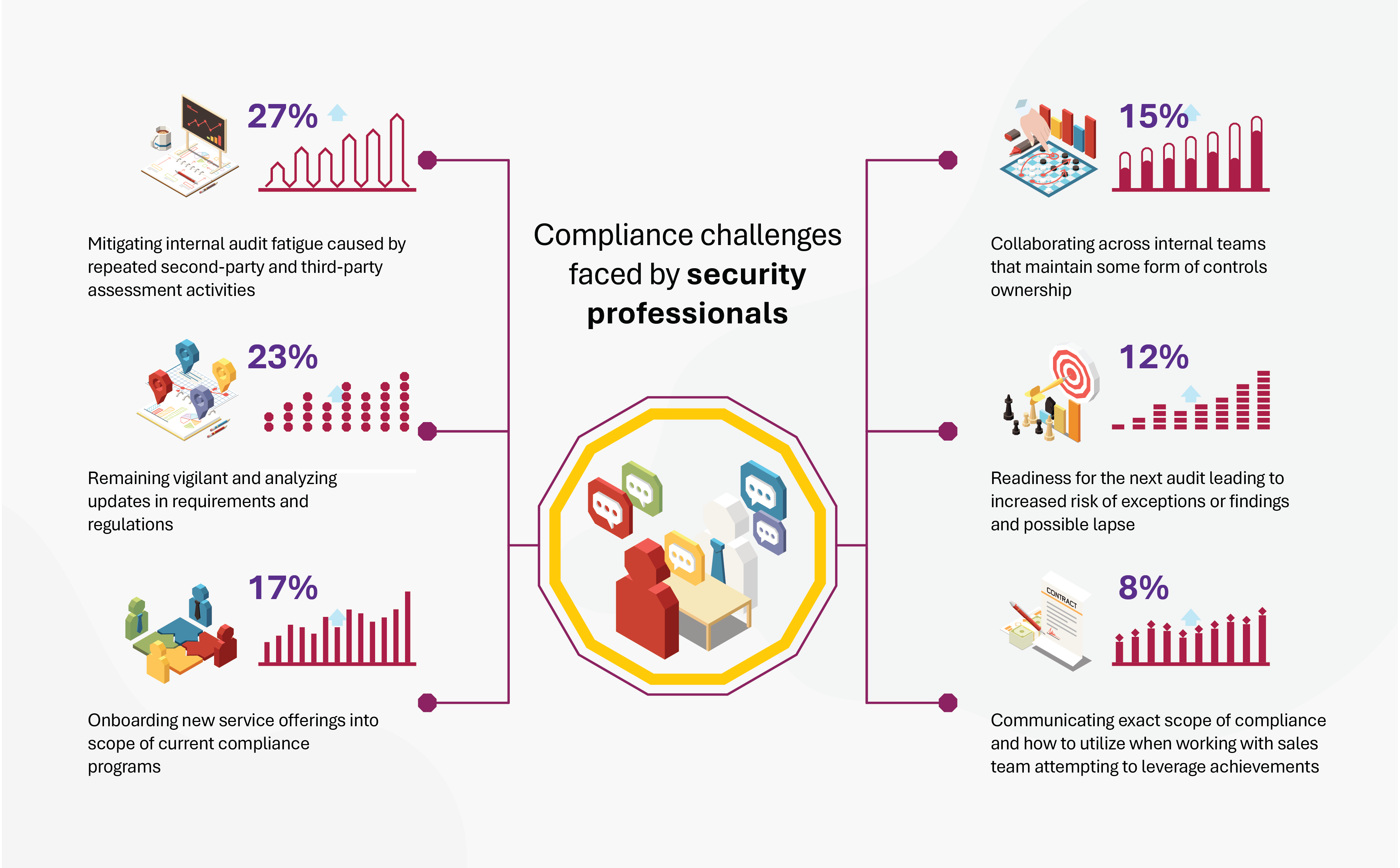
Non-compliance doesn’t just put organizations at risk financially and reputation-wise; it also hinders research and innovation by limiting data use.
This is where a comprehensive framework like HITRUST CSF comes in. HITRUST framework integrates security, privacy, and risk management practices into a cohesive approach.
So, if you are in the healthcare industry and facing these challenges, consider adopting a unified framework to secure your data and keep your operations running smoothly.
This blog delves into the technical application of the HITRUST certification and framework in different aspects of protecting healthcare data and systems like encryption, access control, identity management, and its integration with healthcare IT infrastructure.
Essential HITRUST CSF Requirements for Securing Healthcare Infrastructure
HITRUST CSF standards are versatile and can be used to protect patient health information in various healthcare systems and platforms while also helping organizations comply with HITRUST risk management regulations.
Encryption: Safeguarding Data in Transit and at Rest
Encryption is a cornerstone of the HITRUST framework, ensuring that sensitive data remains secure whether stored or transmitted. The HITRUST CSF explicitly requires the following to achieve certification:
- Data at Rest Encryption: Organizations must employ AES-256 encryption (standard encryption method used in cloud) for databases, file systems, and backup media. This includes encrypting electronic protected health information (ePHI) stored on devices and ensuring that decryption keys are protected through robust key management systems.
Example: Encrypting a hospital’s patient record database ensures that even if a hacker gains unauthorized access to the server, the data remains unreadable. This helps protect patient confidentiality and comply with regulatory mandates.
- Data in Transit Encryption: HITRUST mandates the use of secure transport protocols, such as TLS 1.3 (advanced encryption for data to secure communication over the internet), for communications involving sensitive healthcare data. This applies to data exchanges between systems, including APIs, email, and web applications.
Example: Using HTTPS to encrypt communication between a patient portal and the server ensures that patient data cannot be intercepted during transmission, protecting against man-in-the-middle attacks.
By meeting these encryption requirements, organizations can effectively mitigate risks such as data breaches and unauthorized disclosures, aligning with HITRUST’s rigorous security standards.
Access Control: Restricting Unauthorized Access
Access control mechanisms are critical to ensuring that only authorized personnel can access sensitive data. HITRUST CSF outlines several specific requirements to enforce access control:
- Role-Based Access Control (RBAC): Organizations must define and implement roles with least-privilege principles. This involves assigning access permissions based on job responsibilities and regularly reviewing these permissions to ensure compliance.
Example: This can be understood with a simple example like assigning read-only access to nurses for patient files while granting full access to physicians ensures that users only access the data they need, reducing the risk of misuse or accidental changes.
- Multi-Factor Authentication (MFA): HITRUST security certification mandates the use of MFA for accessing sensitive systems and applications. This adds an additional layer of security by requiring users to verify their identity through at least two factors, such as passwords and biometric data.
- Periodic Access Reviews: HITRUST requires organizations to conduct regular access reviews to identify and revoke unnecessary privileges. This helps minimize the risk of insider threats and unauthorized access.
Example: Conducting quarterly audits to remove terminated employees’ accounts reduces the risk of unauthorized access through dormant accounts.
Implementing these access control measures ensures compliance with HITRUST standards and strengthens the overall security posture of healthcare IT environments.
Identity Management: Strengthening Authentication and Accountability
Identity management systems form the foundation of secure user authentication and accountability in HITRUST-compliant organizations. To meet HITRUST CSF requirements, organizations must focus on the following:
- Identity Verification: HITRUST requires robust identity verification processes to ensure that users are who they claim to be. This may include pre-employment background checks and identity proofing during onboarding.
- Single Sign-On (SSO): HITRUST encourages the use of SSO to streamline authentication while maintaining strong security. SSO reduces the risk of password fatigue and associated vulnerabilities.
Example: Using SSO in a hospital’s multiple systems enables doctors to log in once to access the EHR, scheduling, and billing systems securely, improving efficiency and reducing password fatigue.
- Audit and Accountability: Identity management systems must integrate with logging and monitoring solutions to track user activities comprehensively. These logs are essential for detecting anomalies, investigating incidents, and demonstrating compliance during audits.
Example: Recording all administrative actions, such as creating or deleting user accounts, helps identify potential misuse and supports forensic investigations.
By adhering to these identity management standards, organizations can enhance accountability and reduce the likelihood of unauthorized access to critical healthcare systems.
There are several critical HITRUST CSF requirements, and complying with them will bring organizations closer to achieving robust security and regulatory compliance.
Values HITRUST Certification Brings to Healthcare
The HITRUST framework is a gold standard to keep healthcare data safe and sound. This creates a roadmap for protecting delicate patient information.
With HITRUST, healthcare isn’t just about meeting regulations, it’s about setting the bar high for secure, patient-focused care in the age of digital transformation.
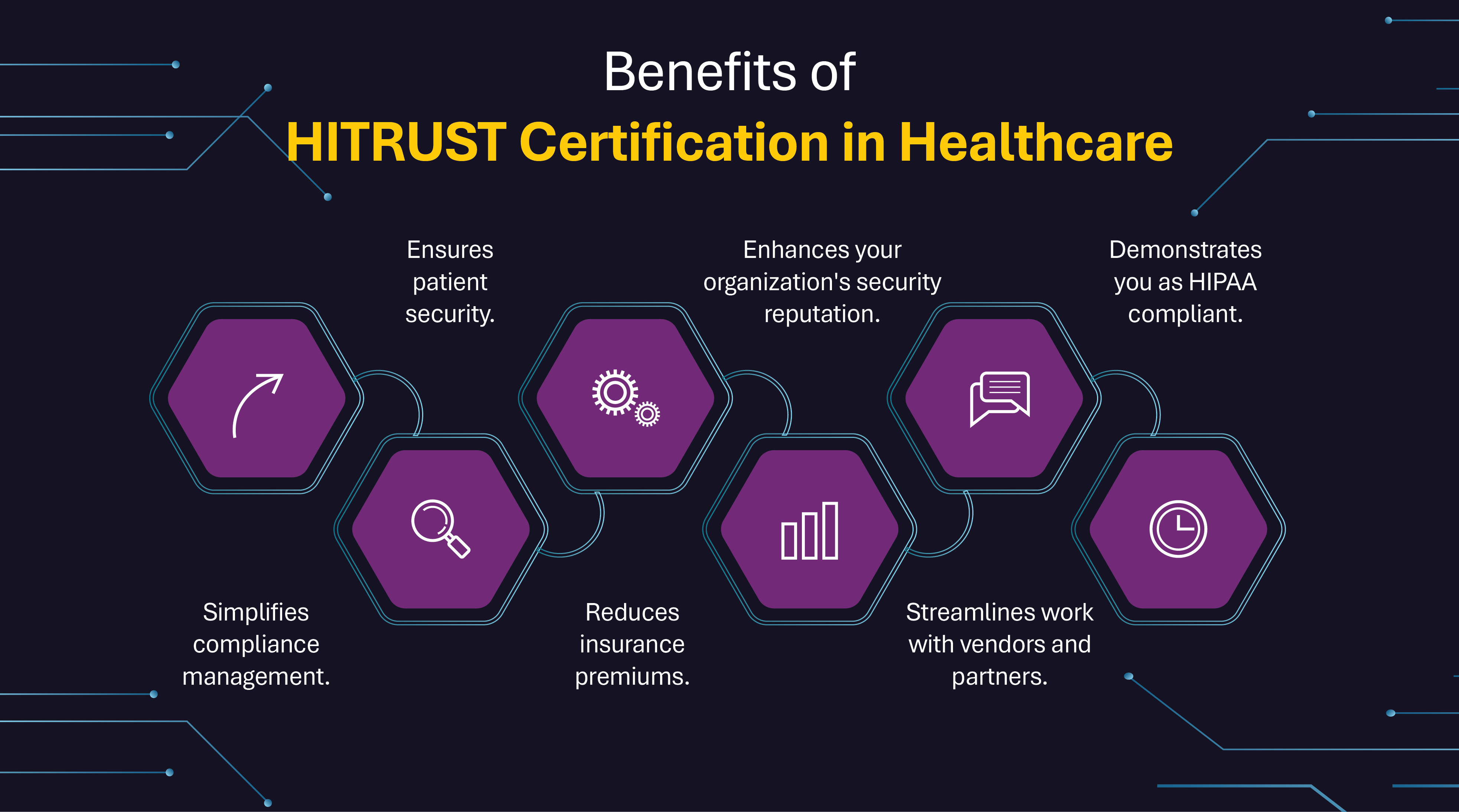
Why Partner with HITRUST Assessors?
Healthcare organizations often face challenges in implementing the HITRUST risk management and security framework due to its technical complexity. Partnering with experienced HITRUST assessors like Network Intelligence streamline the certification process. They help you by:
- Identifying areas of non-compliance.
- Developing customized implementation roadmaps.
- Conducting readiness assessments and more.
Why Choose Us for HITRUST Compliance?
Network Intelligence specializes in providing end-to-end HITRUST risk management and security requirements, making the certification process seamless and efficient.
We leverage a comprehensive approach tailored to healthcare organizations, ensuring every step aligns with HITRUST CSF requirements. From initial gap analysis to final certification, we handle every aspect, including:
- Customized Compliance Roadmaps
- Technical Implementation Support
- Audit Preparation and Validation
Connect with our experts to secure your sensitive data and achieve compliance with confidence. Let us help you navigate the complexities of HITRUST certification, so you can focus on delivering exceptional healthcare services.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
