In today’s evolving threat landscape, CISOs face a seemingly impossible challenge: strengthen security while cutting costs. After extensive research and conversations with security leaders, we believe that not only is this possible – it’s an opportunity to build a more resilient security program. Here’s how we’ve helped clients do it right.
Strategic Cost Optimization: The Smart Way Forward
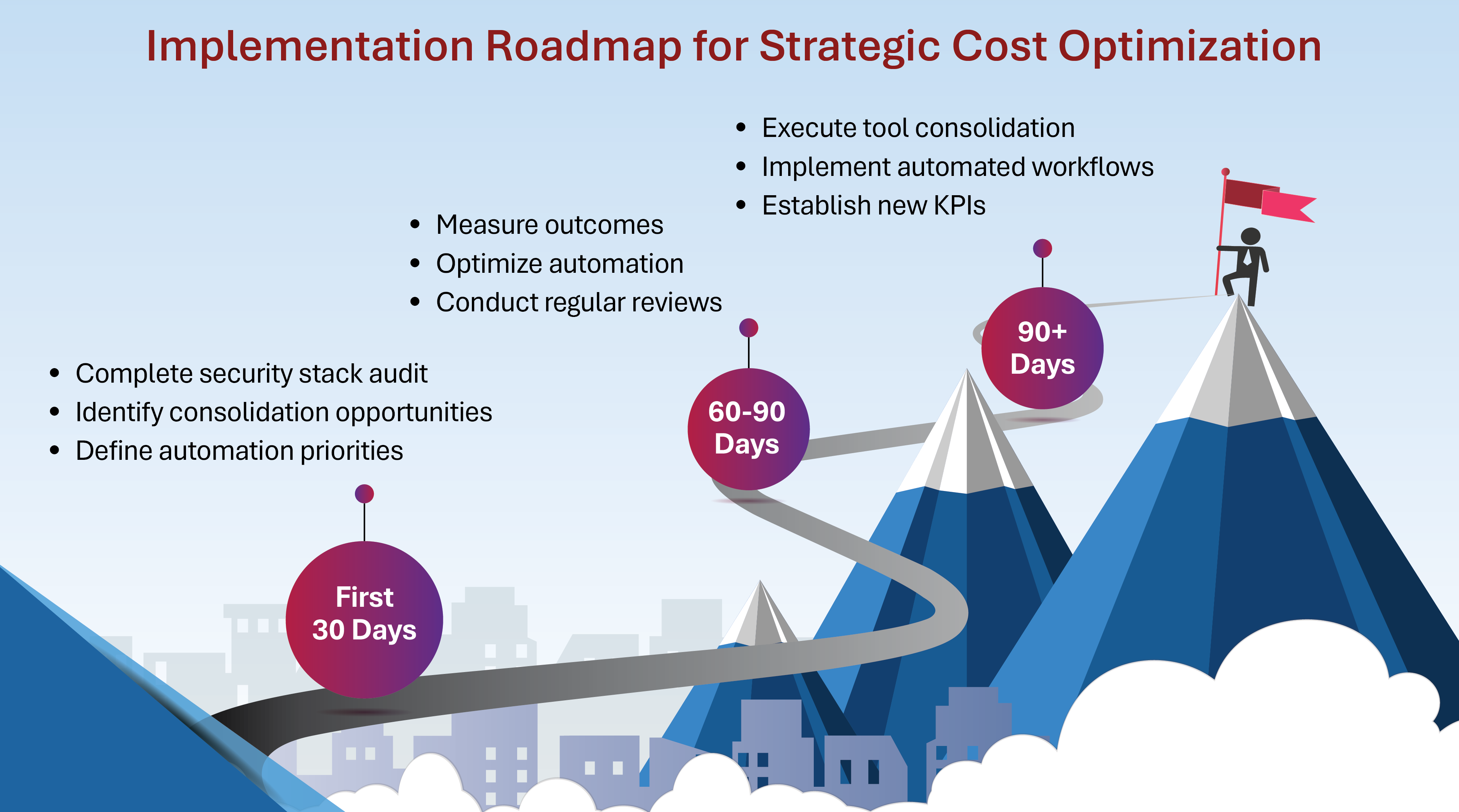
1. Audit Your Security Stack (The 80/20 Rule)
According to IBM Security’s “State of Security Operations 2024”, 49% of organizations use between 6 and 40 security products, with 98% managing these through multiple consoles. This fragmentation creates both cost inefficiencies and security vulnerabilities.
Practical Tips:
- Conduct a thorough audit of your security tools
- Identify and eliminate tool redundancy
- Focus on core capabilities that align with your security strategy
- Evaluate integration capabilities with your existing security infrastructure
Research from Gartner’s cybersecurity analysis team suggests most organizations can reduce their security tool count by 20-30% while improving their security posture through strategic consolidation.
2. Embrace Prevention-First Security
The latest IBM Cost of a Data Breach Report 2024 reveals that organizations leveraging AI and automation save an average of $3.05 million per breach compared to those without these capabilities. The key is focusing on prevention rather than just detection.
Prevention-First Priorities:
- Advanced threat prevention capabilities
- Automated response mechanisms
- AI-powered predictive security measures
- Zero-trust architecture implementation
3. Optimize Human Capital
Deloitte’s Cyber Budget and Resource Allocation Report 2024 shows that small businesses typically allocate 4-10% of their IT budget to cybersecurity, while enterprises often spend 10-20%. However, the focus should be on resource effectiveness rather than just spending levels.
Resource Optimization Strategies:
- Define core in-house competencies
- Evaluate managed service opportunities
- Implement automation for routine tasks
- Establish clear performance metrics
4. Build a Risk-Based Security Program
A comprehensive study by Forrester Research titled “The Total Economic Impact™ Of Zero Trust” demonstrates that organizations implementing Zero Trust have seen up to 92% ROI with payback periods under six months. The key is aligning security spending with actual risk exposure.
Risk Optimization Framework:
- Implement FAIR (Factor Analysis of Information Risk) modeling
- Prioritize investments based on business impact
- Conduct regular risk assessments
- Establish clear security ROI metrics
5. Leverage Automation Strategically
McKinsey & Company’s latest research on “The Future of Cybersecurity Operations” indicates that proper security automation can reduce incident response times by 50-80% while improving accuracy.
High-Value Automation Targets:
- Security alert triage
- Vulnerability management
- Access control administration
- Continuous security testing
The Bottom Line
As we navigate through 2025, the cybersecurity landscape continues to evolve rapidly. Success isn’t about having more tools – it’s about having the right tools, used effectively, by well-trained people, following smart processes.
Remember: The most successful security programs aren’t always the most expensive – they’re the ones that align security spending with business objectives and real-world risks.
Author
-

Ashwany Pillai is the Global Head of Marketing & Inside Sales at Network Intelligence, driven by a passion for cybersecurity marketing. With over 15 years of experience spanning healthcare, B2B SaaS, and IT, he brings extensive knowledge and versatility. His dedication to staying at the forefront of the industry is demonstrated by certifications from LinkedIn, SEMrush, Google, and HubSpot Academy in Digital Marketing, SEO, and Content Marketing. Ashwany excels in crafting innovative campaigns through influencer engagement, data-driven strategies, and cutting-edge marketing techniques.
View all posts
