One of the most critical factors that determine the success and efficacy of a digital forensic investigation is putting together the right temporal analysis of events. At a fundamental level, the Windows Timeline is nothing but putting the what and when together of the user’s activities on a Windows system. The Windows Timeline is an excellent tool that helps in digital forensic analysis.
What is Windows Timeline?
Windows Timeline was introduced in the April 2018 update. The functionality is hosted from the taskbar or can be alternatively accessed via a shortcut of Windows keys. Timeline helps us travel in time to view the user’s current or past activities, keep track of them, and switch between desktops.

Figure 1: The Task View icon from which the user can access the Timeline feature.
By default, the Timeline showcases the user activity snapshots on a specific date and time
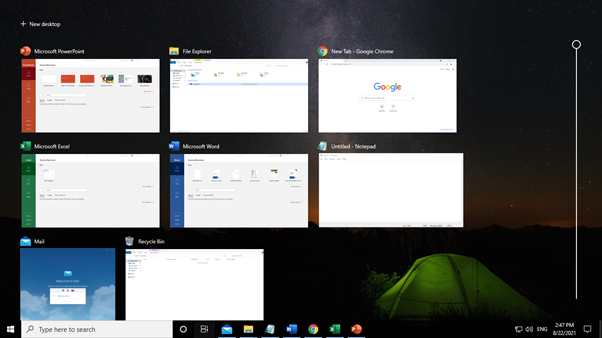
Figure 2: The currently available applications that are open.
Timeline can store the records of activities and events for 30 days. Users can remove the record of a particular activity or disable the timeline feature altogether, as shown below.
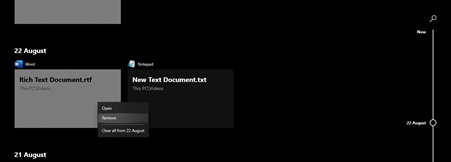
Figure 3: Steps for removing a particular activity on a given day from the Timeline.
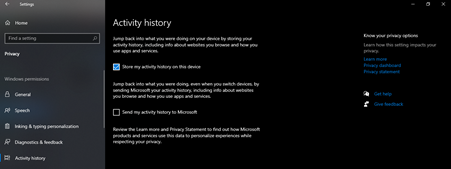
Figure 4: Toggle off the ‘Show my activity history’ option to permanently disable the timeline feature.
How does Windows Timeline work?
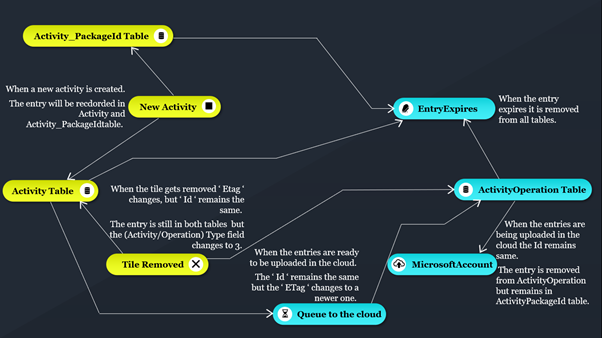
Figure 5: Workflow of Windows Timeline.
The user activity information in Windows 10 Timeline is saved to the file ActivitiesCache.DB with the following path:
\Users\%profilename%\AppData\Local\ConnectedDevicesPlatform\L.%profile name%\.
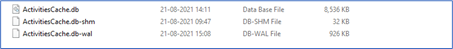
Figure 6: The list of files in which past-activity information is stored.
ActivitiesCache.db is an SQLite database (version 3). Like any SQLite database, it has two supplementary files ActivitiesCache.db-shm and ActivitiesCache.db-wal.
ActivitiesCache.db contains the following tables.
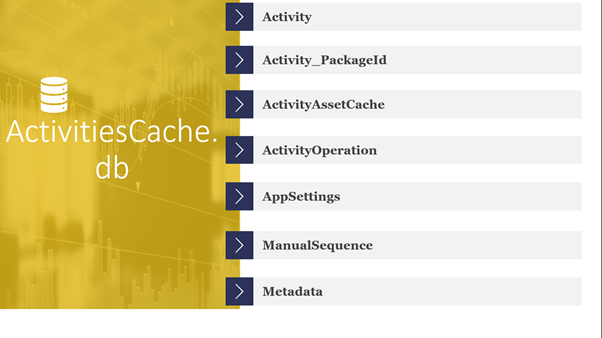
Figure 7: List of tables within ActivitiesCache.db
The two tables which hold the most valuable information is ActivityOperation and Activity.
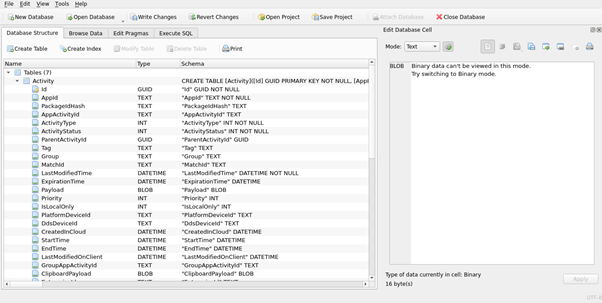
Figure 8 : Activity table with AppId, AppActivityId, ActivityType, ActivityStatus, ParentActivityId, etc.
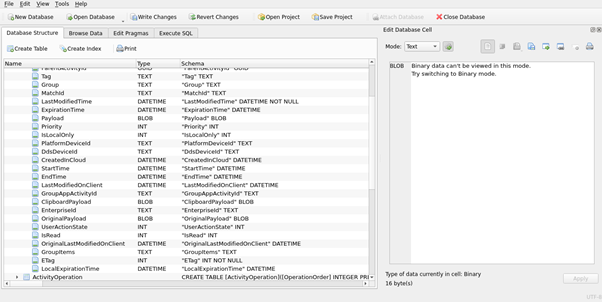
Figure 9 : Activity table with StartTime, EndTime, GroupAppActivityId, ClipboardPayload, etc.
Most of the fields between the two tables, The activity table, and ActivityOperation are somewhat similar. For instance,
- The ID field which holds the unique GUID value for each activity is the same.
- The ETag field is an integer type, and each activity can have multiple ETag values.
- PackageIdHash is a unique value assigned to the application, and it changes its value for different versions of the same application, and the nature of it is determined to QuickXorHash.
ActivityStatus (Activity table) and OperationType (ActivityOperation table)
ActivityStatus , as the name suggests, indicates the status of the activity, which is represented in numbers
‘ 1 ‘ indicates the activity is in use and still an open application.
‘ 2 ‘ indicates the entry is updated with a previously Active entry.
‘ 3 ‘ indicates the Tile is removed from the Timeline.
‘ 4 ‘ indicates the entry is ignored.
CreationTime represents the Activity Creation Time. LastModifiedTime indicates the time when the activity was modified. ExpirationTime marks the time left for the activity to expire. All the Time fields are represented in the Epoch time format.
AppId
The AppId consists of two main components, namely, application and platform. The application describes the kind of application currently running, such as VirtualBox, Slack, etc.
The Platform field includes the following:
‘ host ‘ indicates if the action was performed by the host machine.
‘ PackageId ‘ and ‘ AlternateId ‘ come with the executable and file path entries.
‘ x_exe_path ‘ indicates standalone executables.
‘ windows_win32 ‘ for Installed Software (non-UWP) Applications.
‘ windows_universal ’ for Universal Windows Apps (UWP). Others include ‘ ios ‘, ‘ android ’ and ‘ web ‘.
Payload
The payload field is a JSON blob and differs for each ActivityType.
ActivityType 5 means a user has opened an application or URL in a web browser.
The Payload entries include,
- Displaytext: The file or URL opened.
- appDisplayName: The program used.
- Description: The full path of the file or URL.
- contentURi: The file or URL’s full path.
- FileShellLinkis The encoded ‘link’ that is used to re-open the same file or URL.
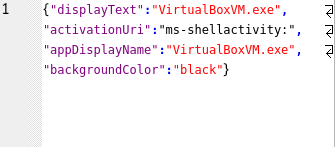
Figure 10: Payload field for Activity type 5
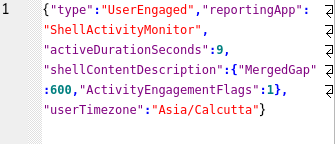
Figure 11: Payload field for Activity type 6
ActivityType 6 means the app used earlier or the app in focus at the moment.
The Payload entries include:
- type: type of activity occurred.
- activeDurationSeconds: The number of seconds the activity was in usage.
- userTimeZone: Timezone of the Device where the activity was generated.
PlatformDeviceId
PlatformDeviceId is the unique Id of the device where the activity was created. We can use this Id to find the device in which the user is operating. The following numbers help us achieve it
- ‘ 1 ‘ Xbox One
- ‘ 6 ‘ Apple iPhone
- ‘ 7 ‘ Apple iPad
- ‘ 8 ‘ Android device
- ‘ 9 ‘ Windows 10 Desktop
- ‘ 11 ‘ Windows 10 Phone
- ‘ 12 ‘ Linux device
- ‘ 13 ‘ Windows IoT
- ‘ 14 ‘ Surface Hub
- ‘ 15 ‘ Windows Laptop
It can be correlated with the respective entry in NTUSER.dat. Suppose we navigate to the respective path via “Software\Microsoft\Windows\CurrentVersion\TaskFlow\DeviceCache\” in the registry editor as shown in the image below and correlate the device type value with the numbers mentioned above. In that case, we can find that in this case, the DeviceType is 15 – Windows Laptop.
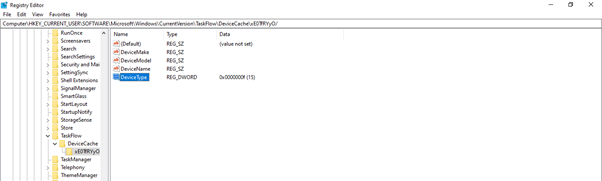
Figure 12: The registry path under DeviceCache where we can find the DeviceType is displayed.
Consider an investigation where we need to find the duration for which an application was run on the machine. In this specific case, let’s check this for the Outlook application. First, we need to note the unique PackageIdHash, ‘ OCpK4J4yE…‘and then fire it in the SQL query as shown in the image below. The SQL query brings up the first ActivityType 5 of the Outlook application, which indicates the start of the application.
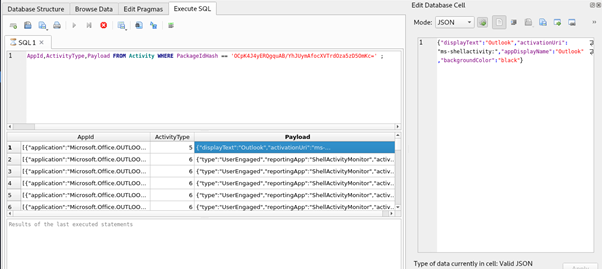
Figure 13: The components of the Payload field corresponding to its ActiveType 5 are displayed.
The following entry is ActivityType6 which is a UserEngaged activity. As we can see from the image below, the Payload field contents on the right side show us the Time Zone, and the activeDurationSeconds is 5 seconds. So, if we keep track of when the application closes and sum up the activeDurationSeconds till that entry, we can find the total seconds the application was used.
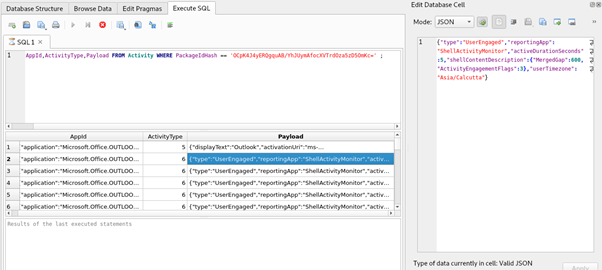
Figure 14: The components of the Payload field corresponding to its ActiveType 6 are displayed.
There are two open-source tools to investigate Windows 10 Timeline; the easiest way is to look at the data contained in ActivitiesCache.db using a WindowsTimeline parser.
WindowsTimeline parser
To load a file in the WindowsTimeline parser tool user needs to go to File -> Select an ActivitiesCache.db and then hit the Run option. It will display the output as shown in the image below.
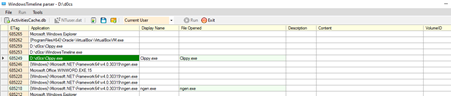
Figure 15: Illustrates WindowsTimeline parser tool to which a database file was provided as input.
We can save the output obtained to our desired folder location in the CSV file by clicking the “Save results” option.
DB Browser for SQLite
Another method is opening ActivitiesCache.db file in an SQLite viewer. Here, we used a tool called DB Browser for SQLite. To open a DB file, we can simply click the Open Database option and select the db file from the folder. To select a particular table from the list of tables available, we need to navigate to Browse Data -> Click the drop-down menu nearby Table option and choose one from the list. In the below image, the AppSettings table from the drop-down menu is selected.
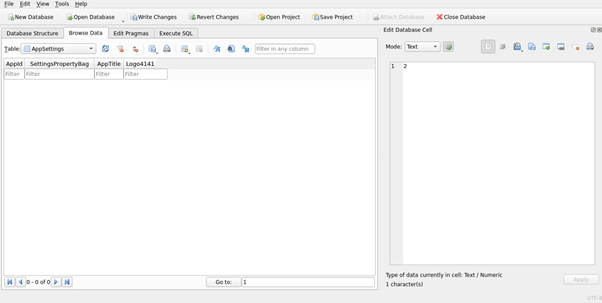
Figure 16: DB Browser for SQLite
Another good tool for parsing the Windows 10 Timeline is Eric Zimmerman’s WxtCMD which can be downloaded from here
Conclusion
The Windows Timeline is an extremely useful tool to reconstruct the events on a device over the previous 30 days. In addition, it provides more information on the files launched in the device, including the deleted ones. Thus, this tool can be a handy aid for digital forensics investigators.
