Part III: Cracking the Lid – Rooting and Unlocking Bootloaders
This is part 3 of building your own mobile pen-testing device. Here’s the link to part 2 and part 1.
Before we get started to cracking our device, let’s take a look at how our end device would look like:
![]() Oneplus One with Alfa NHR in monitor mode
Oneplus One with Alfa NHR in monitor mode
 Full-fledged Kali with xfce environment running on Oneplus One
Full-fledged Kali with xfce environment running on Oneplus One
So let’s get started and let me clear a few android terminologies that I will be using throughout the blog:
- Data – This means application data such as contacts, cookies, applications installed, system partition and saved information. This doesn’t include photos or videos. Data is always stored in the Phone memory. (unless they are stored within the application’s data directory)
- Unlocking – This is basically bootloader unlocking and not lockscreen unlocking.
- Phone Memory – This is the place where system files are stored. (consider this to be like a Windowsx86 folder from windows C: drive)
- Internal Memory – This is the place which is left after the partition from Phone memory. More likely where we store our data without an sdcard. (Consider this to be like your C: drive)
- External Memory – This is our external sdcard.
Now since we have our basics cleared, let’s proceed to unlocking and rooting our cell phones. Remember, there is a high risk in unlocking the bootloader of your device. Make sure you have an Oandbackup backup or atleast you backup your data before we start cracking our device. Most of the bootloaders have a security feature that whenever you unlock the bootloader, it wipes your entire device. Once you have your backup, enable USB debugging by navigating to settings and doing the following: –
 Settings -> About phone -> Build Number (hit 5 times) -> Settings (Scroll Down) -> Developer Options -> Android Debugging
Settings -> About phone -> Build Number (hit 5 times) -> Settings (Scroll Down) -> Developer Options -> Android Debugging
Now you need to install proper drivers to make your laptop recognize the adb drivers of your cell phone device. You can install the whole SDK for windows from here which contains the adb drivers for all of the devices. However, I prefer to user Linux(Debian) on my machine. For Linux systems, one can simply type ‘apt-get install android-tools-adb android-tools-fastboot’ onto their terminal. This will install all the necessary drivers for all the cell phones. Once installed, connect your device to your laptop, navigate to terminal (or cmd for windows), and type ‘adb devices’. It should show you your connected device. After that simply type ‘adb reboot bootloader’ to boot your phone in fastboot mode.
Once, in fastboot mode, type ‘fastboot devices’ to check if your device is detected. Once detected, type ‘fastboot oem unlock’ to unlock your device. Now, this method is basically universal for most of the phones. But this may not work in case your device has extra security, especially for HTC, Xiaomi, Sony and Motorola phones. I tend to use Oneplus One, where the above commands unlock my device. For Sony phones, you would require a key which you could get only by mailing your first 15 digits of your IMEI to their respective email support. More information about unlocking Sony devices can be found here. For other devices which do not support the above simple oem unlock, you would have to type ‘fastboot oem get_unlock_data’ OR ‘fastboot oem get_identifier_token’ (*differs from phone to phone). Once you get your unlock hash, you would need to send them to your manufacturer’s support email, and they will give you the unlock key. Once you have the key, you can simply type ‘fastboot oem unlock <type_your_unlock_key_here>’.
 Unlocking Sequence (same for windows and linux)
Unlocking Sequence (same for windows and linux)
Once your cell phone is unlocked and booted, next thing we need to do is root your device. So, there are two methods that I follow, through which I have managed to unlock almost every other device till date and so should you be able to.
The Easy Way
First method is to download the TWRP recovery and flash it via fastboot. Download the TWRP recovery from here and download SuperSU from here. Once downloaded, again reboot your device to fastboot mode as we did before, and type the following commands ’fastboot flash recovery twrp.img’. (For some devices, you may need to rename the twrp.img to recovery.img). Once flashed, type ‘fastboot reboot’ to reboot the device.
 Flashing TWRP recovery via fastboot mode
Flashing TWRP recovery via fastboot mode
Now when your phone reboots, type ‘adb reboot recovery’ to reboot your phone into the recovery mode. Here, select Install Zip, browse through the directory and select the previously downloaded SuperSU.zip file, and swipe right on the screen to flash it. Once done, reboot your device and it should be rooted.
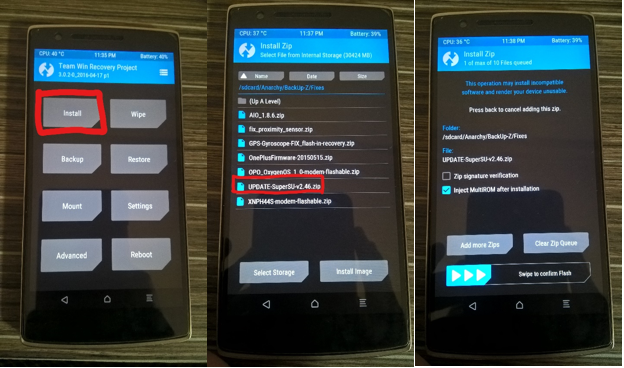 Flashing SuperSU zip file via TWRP Recovery
Flashing SuperSU zip file via TWRP Recovery
The Hard Way
Now, for most of the people the first method should have sufficed. But in case, your device is still not rooted, then we would have to proceed the hard way. Once you have unlocked your bootloader, wipe off all the data and do factory reset, and delete all the data from your internal and external memory(*important). Now, we will be rooting our phone with Kingroot. Kingroot is a SuperUser manager, similar to SuperSU, but is known to be a somewhat malicious application in addition to throwing lots of adware to the users. Make sure your cell phone device is not connected to internet when doing this. Kingroot is from China and is an awesome app to root any device that you want, but comes with its own set of disadvantages. This is the reason why this app isn’t available on Google Playstore. Another disadvantage is that Kingroot only gives you temporary root access. Once your phone is rebooted, the root access is gone. This is the reason why we will only be using Kingroot to root our device, and once its rooted, we will replace the binaries and the app with that of the SuperSU. You can download Kingroot from here. Install the Kingroot apk, download the SuperSU apk from here and Busybox from here. Don’t install the other two yet, coz it simply won’t work that way. Kingroot won’t allow us to install the SuperSU binaries till we remove Kingroot. Once the Kingroot apk is installed, install Jackpal terminal emulator from here. Fire up the terminal, download the su binary and the shell script root.sh from here. Once Downloaded, copy all of them into a single folder and execute the shell script by typing:
$ ‘su –c ‘sh root.sh’.
So, in short what this script basically does is that since we cannot remove the Kingroot directly without losing our root access, we simply start removing the binaries of the Kingroot from the system partition, and replace them with the SuperSU binaries. Also, Kingroot is smart enough to remove SuperSU binaries as well. So, once we copy our binaries, we also change the attributes to make our SuperSU binaries read-only. This way Kingroot won’t be able to delete our file, and finally we should have replaced the Kingroot by the end of the script. Also, we are disabling the stock recovery here, since some firmwares have a tendency to flash stock recovery back when booting and then boot the device. There might be some cases, where you may face errors, so you might have to manually copy the above commands into a terminal and check it. And when doing so, wherever you face any error, just remount the system partition in read-write attribute with the ‘mount -o rw, remount /system’ command and it would work perfectly. Remember, Kingroot is a privilege escalation exploit, and not a commonly used way to gain root access. So, unless you know what you are doing, its recommended to always use official guides from www.xda-developers.com to root a device.
So, since our device is now rooted, we will start building our kernels from the next blog. And always remember to perform TWRP backups from the recovery, so as to restore our phone back to as it was in case something goes wrong.

https://fortniteskin.8b.io
Very energetic blog, I loved that a lot. Will there be a part 2?|