Free Consultation
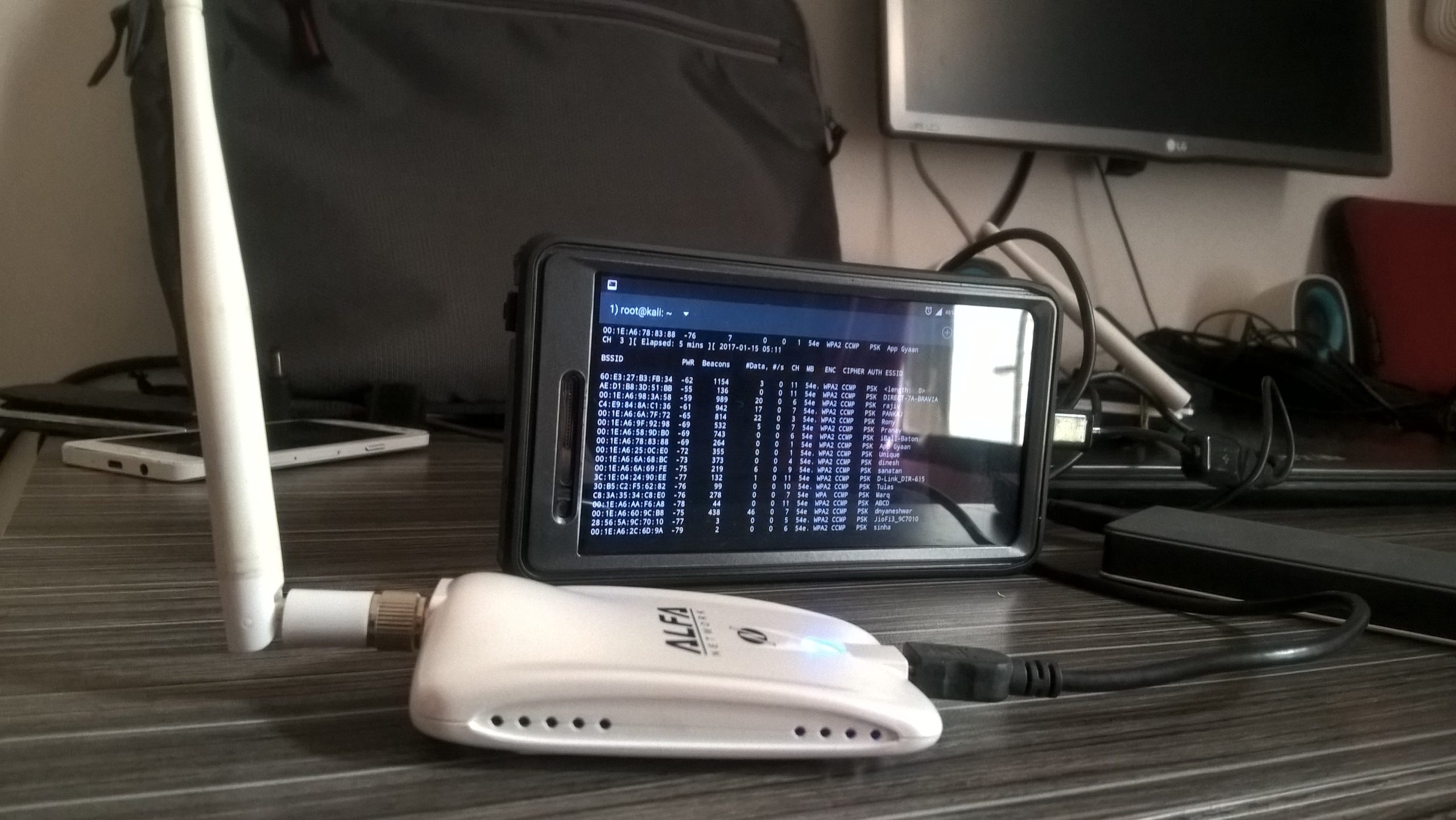
Solving Telecom Security’s most Challenging Cybersecurity Problems
Securing 5G networks, IoT infrastructure, and implementing Zero Trust


The top three problems that telecom companies face are embedding security in the enterprise IT architecture (74%), inadequate management support (64%), and keeping pace with fast-changing cyber technologies (61%).
Since 2001, we have established ourselves as a reliable cybersecurity partner, serving over 500 clients across more than 35 countries, including prominent global telecommunications leaders.
Turnkey Telecom
Cybersecurity Projects

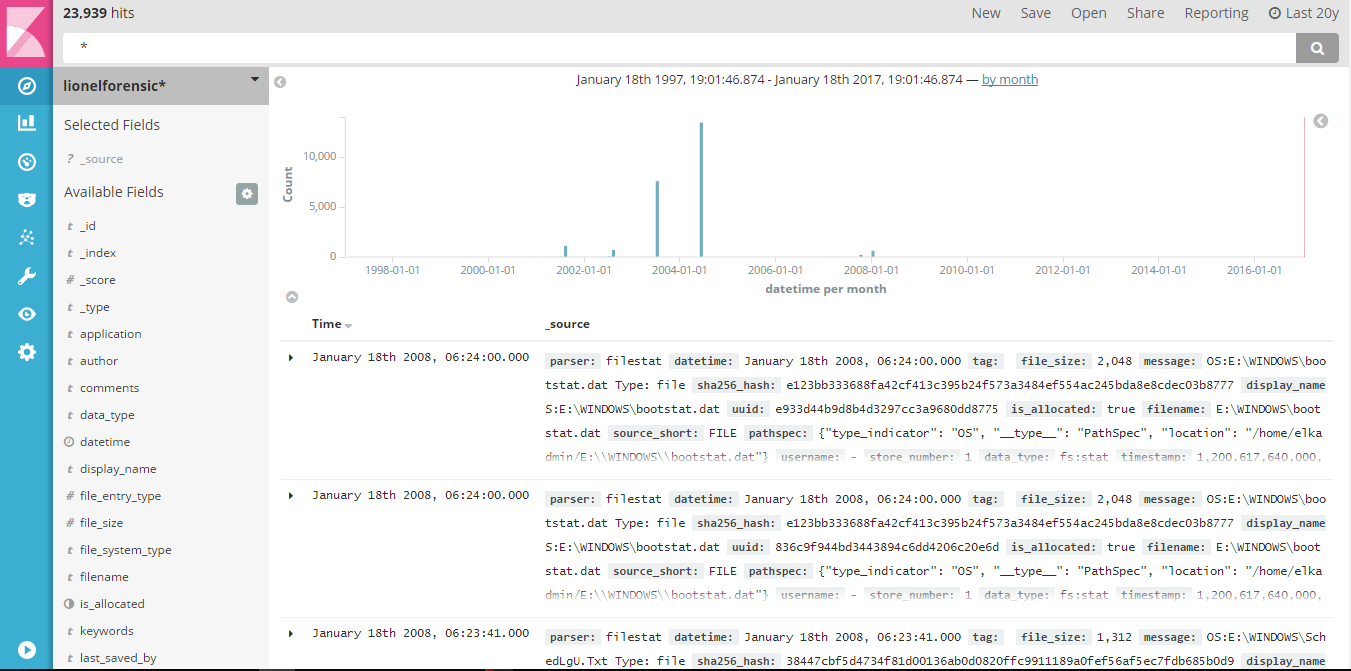
Automating cybersecurity with LLMs
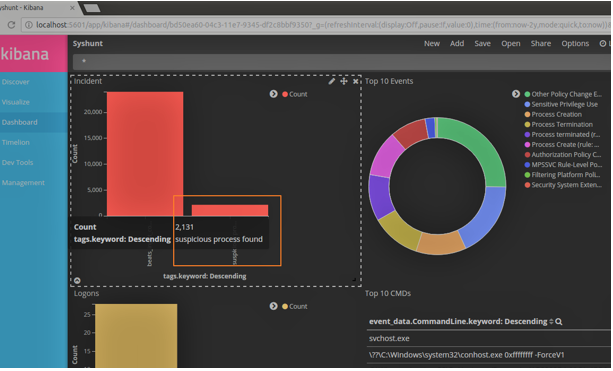
Implementing Zero Trust with CyberArk on the 5g and 4g networks

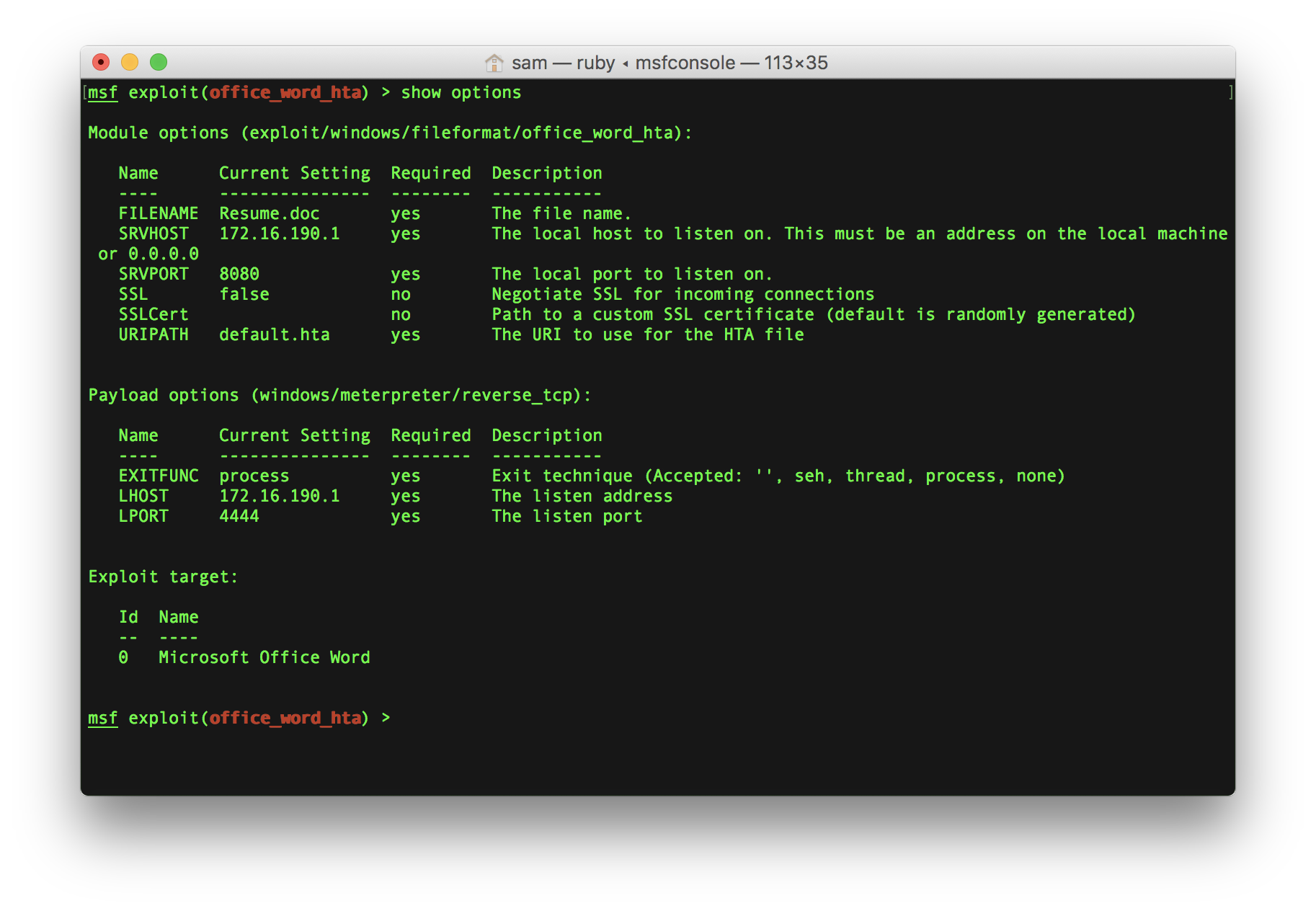
Shifting security left in digital transformation projects

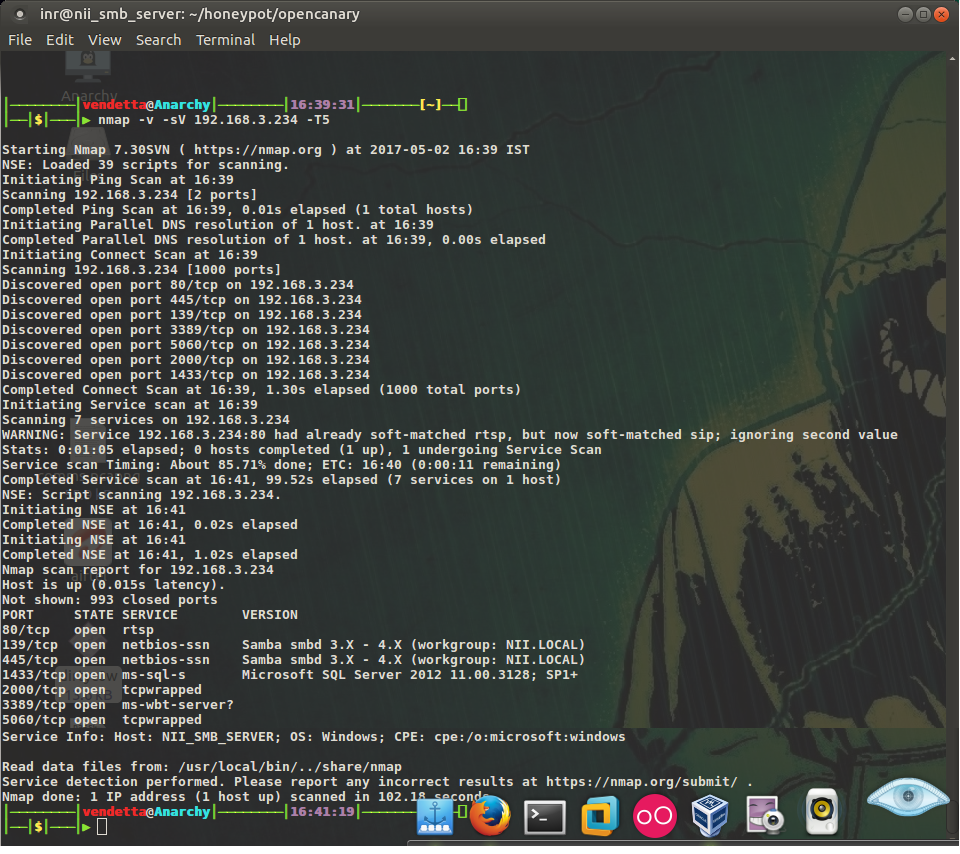
Securing IoT architecture and infrastructure

Achieve compliance at lower costs
600+
Security Professionals
24/7
Premium support on Global SOC Coverage
Ranked amongst the
Top 50 MSSPs
globally
Deep expertise in
5G and IoT
security assessments
Resources


Trusted by Industry Leaders






Trusted by Industry
Leaders






Testimonials


We couldn’t have done this without NI. Their expertise in HITRUST was evident from day one. You gave us a clear plan, worked through the tough parts, and helped us build customer trust.
VP of Cybersecurity
Financial Institution, New York, USA


HITRUST certification felt overwhelming until we partnered with NI's team. They simplified the entire process, addressed every challenge, and got us certified faster than we imagined. Honestly, this certification has transformed how we manage patient data security.
CISO
Healthcare Provider, California, USA


We couldn’t have done this without NI. Their expertise in HITRUST was evident from day one. You gave us a clear plan, worked through the tough parts, and helped us build customer trust.
VP of Cybersecurity
Financial Institution, New York, USA


HITRUST certification felt overwhelming until we partnered with NI's team. They simplified the entire process, addressed every challenge, and got us certified faster than we imagined. Honestly, this certification has transformed how we manage patient data security.
CISO
Healthcare Provider, California, USA


We couldn’t have done this without NI. Their expertise in HITRUST was evident from day one. You gave us a clear plan, worked through the tough parts, and helped us build customer trust.
VP of Cybersecurity
Financial Institution, New York, USA
Schedule a free consultation with a Network Intelligence security expert.

Network Intelligence delivers a comprehensive suite of AI-powered cybersecurity solutions built on the ADVISE framework. This framework ensures we can effectively assess, design, visualize, implement, sustain, and evolve your organization’s security posture.
- Youtube
Contact Us
© Network Intelligence – All rights reserved | Terms & Conditions | Privacy Policy