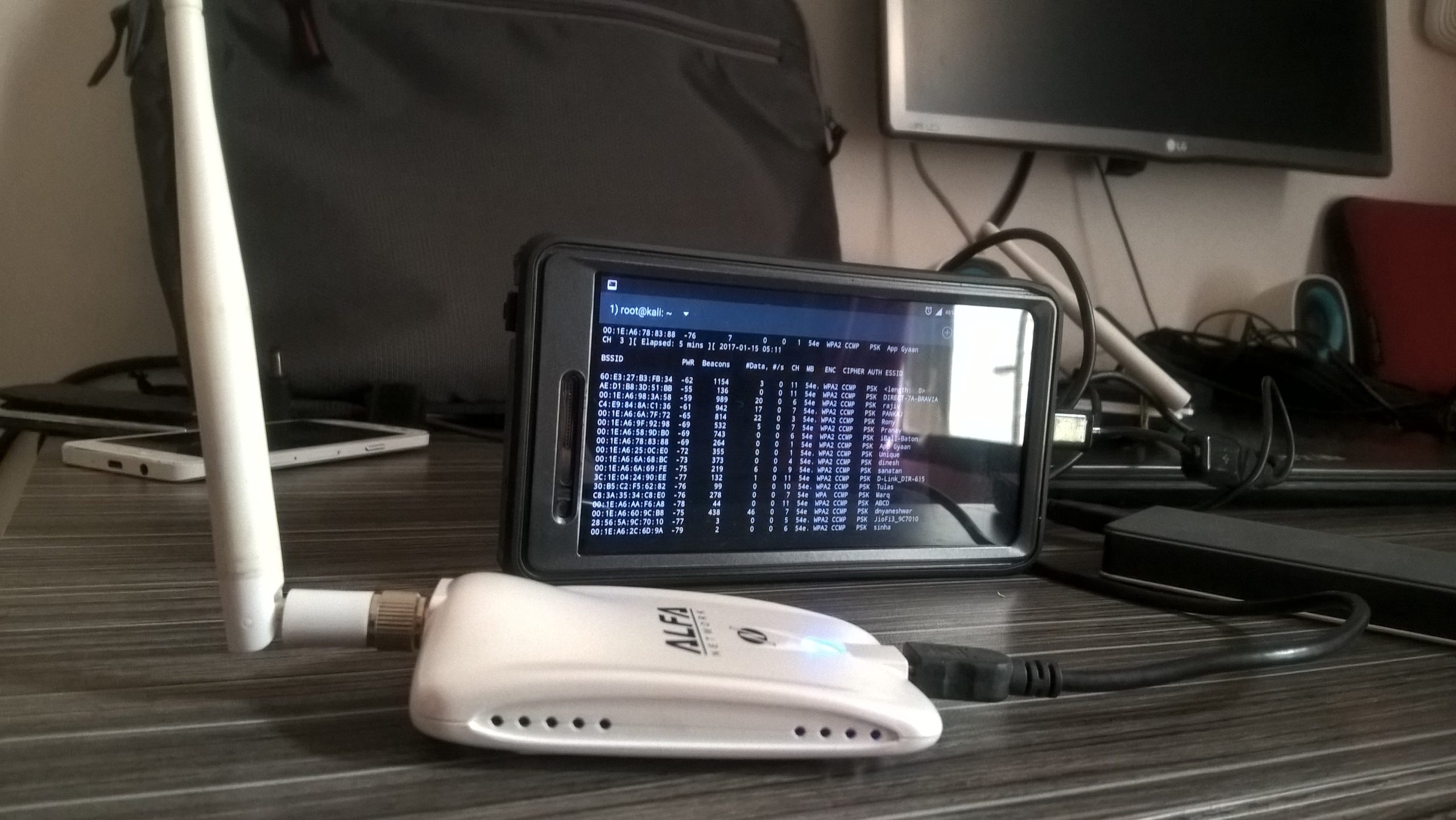
The Mobile Pentesting Device: Birth of Anarchy
Part I: The Prologue – Android rooting Background In the game, Watchdogs, the hacker ‘Aiden Pierce’ uses his cell phone […]

Part I: The Prologue – Android rooting Background In the game, Watchdogs, the hacker ‘Aiden Pierce’ uses his cell phone […]
It is a common technique for criminals to target gaming applications as a propagation vector for malware distribution. Recently, I observed just such a malicious Android app, which acted as an interesting information stealer and then self-destructed. I took this case to investigate further as an interesting research.
For my research, I chose to analyze a popular Android application for malwares. But why select a Russian version? Well, […]
Overview I had to do the risk analysis of the Android 2.2 – Froyo based appliance and check for any […]