SAP is a software suite that offers standard business solutions; it is used by thousands of customers across the globe to manage their businesses to manage financial, asset, and cost accounting, production operations and materials, personnel, and many more tasks.
This blog post provides a methodological overview and a comprehensive approach for SAP penetration testing along with an overview of the security vulnerabilities which are typically present in an SAP environment. To perform a comprehensive security assessment of any technology, it is very important to understand that technology, the purpose of it, its various functions, its dependencies, installation and implementation details, etc. Therefore, this article is sectioned into the following parts:
Part I of the article provides insights on a technical overview of SAP
Part II of the article summarizes the Black Box approach of penetration testing an SAP system
Part III of the article summarizes the Grey Box approach to penetration testing an SAP system
SAP Pen-Testing Part I – A Penetration Tester Meets SAP
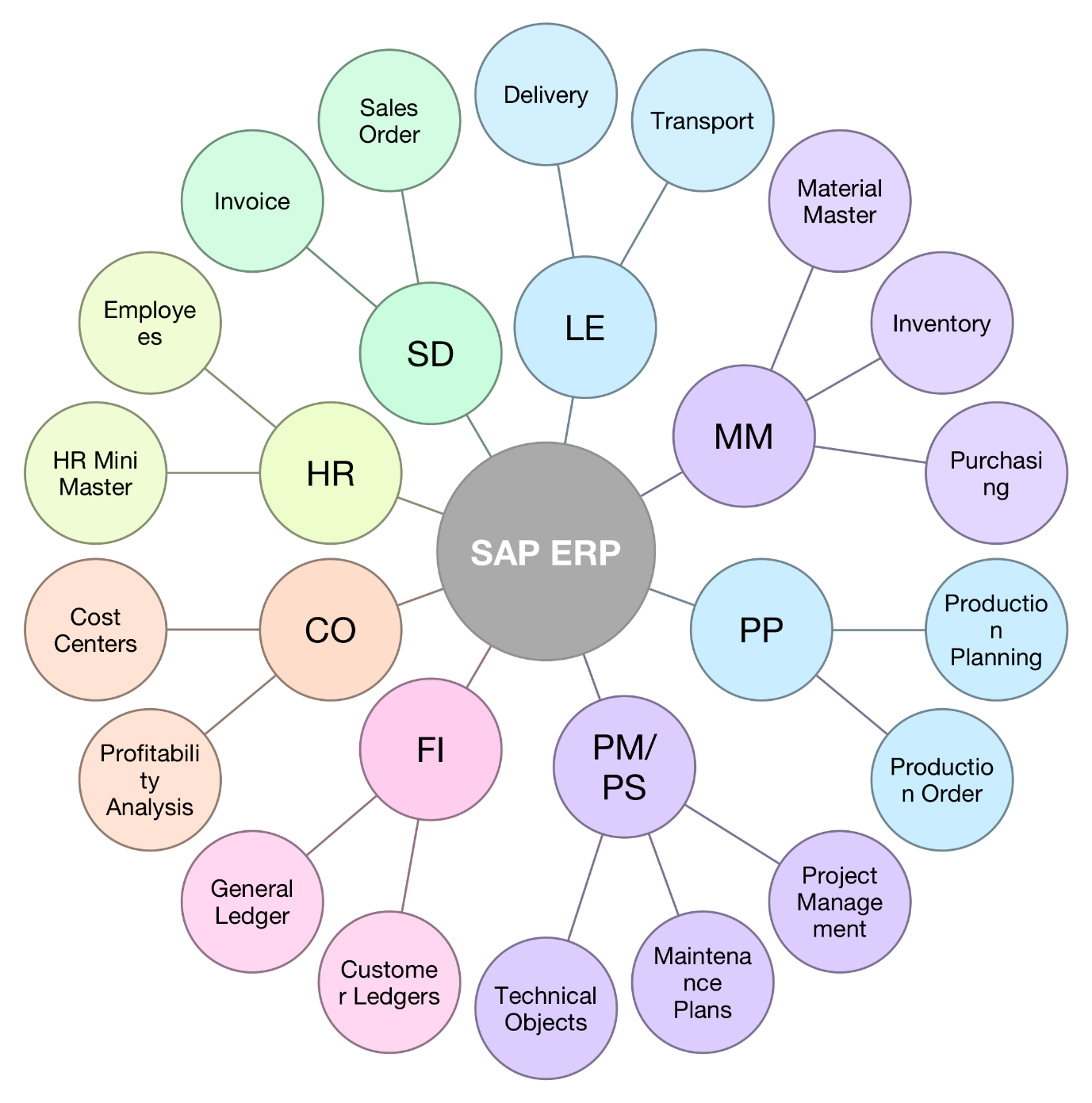
1.1 SAP Modules
SAP is categorized into Functional & Technical modules:
Functional Modules – SAP modules that provide predefined standard functionality to replicate actual business activity are called functional modules. A functional consultant has to interact with the client, understand the business requirement, and use the standard functionality provided by SAP.
Some of the most prominent SAP Functional Modules are:
- SAP HRM – Human Resources Management, also known as Human Resources (HR) or Human Capital Management (HCM)
- SAP PP – Production planning
- SAP MM – Material Management
- SAP QM – Quality Management
- SAP PM – Plant Maintenance
- SAP FICO – Financial Accounting and Controlling
- SAP SD – Sales and Distribution
- SAP FSCM – Financial Supply Chain Management
- SAP PS – Project System
SAP Technical Modules do not directly replicate actual business activity but provide needed support to functional modules. A technical consultant is a programmer who helps the functional consultant to alter the system in few areas to meet specific client business needs. Prominent technical modules are:
- SAP base
- SAP security
- SAP ABAP – Advanced programming of business applications
- SAP HANA – High-performance analytical device
- SAP NetWeaver
- SAP IS – Information Systems (SAP IS)
- SAP XI – Exchange infrastructure
- SAP SolMan – Solution Manager
Some modules are further categorized based on different factors. Different types of SAP modules integrate with each other to create the SAP Solution in an organization.
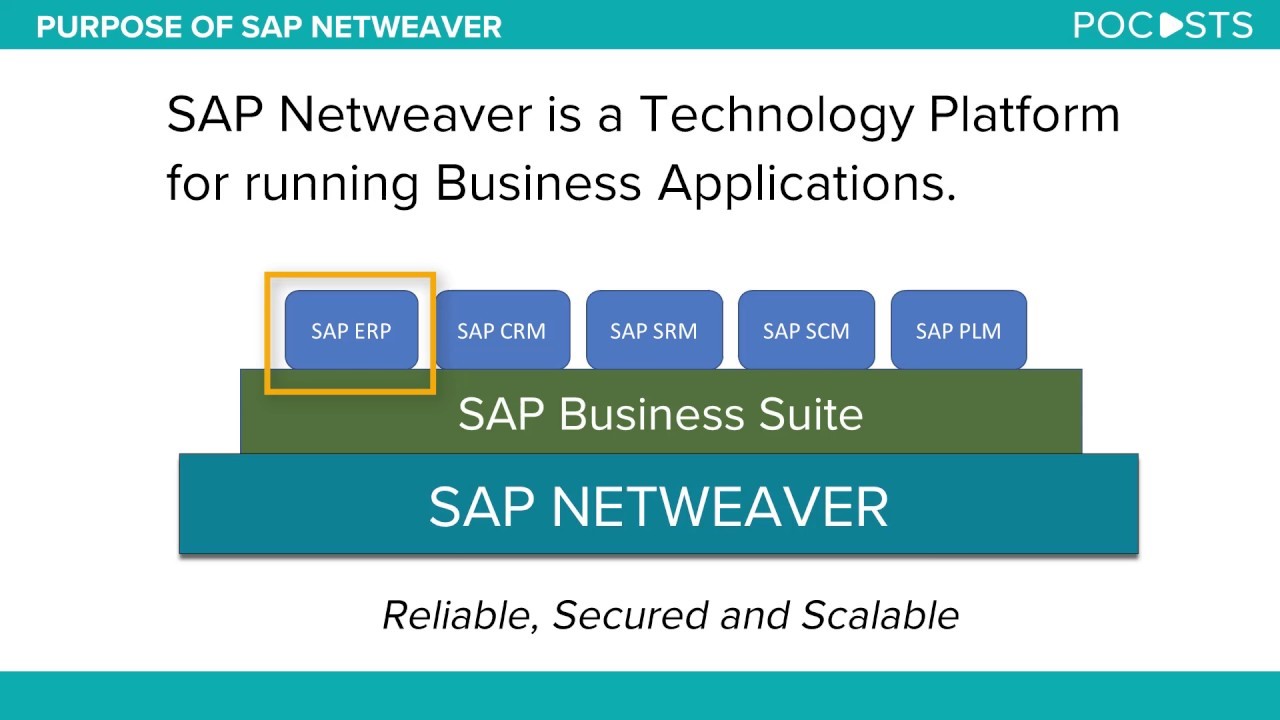
1.2 SAP Products
SAP Business Suite
SAP Business Suite – is a collection of fully-integrated applications with SAP components:
- SAP CRM (Customer Relationship Management)
- SAP ERP (Enterprise Resource Planning) – Alias ERP Central Component (ECC)
- SAP PLM (Product Lifecycle Management)
- SAP SCM (Supply Chain Management)
- SAP SRM (Supplier Relationship Management)
- SAP BW (SAP Business Information Warehouse)
These are the components you are most likely to encounter during a penetration test.
Note: There is a meager difference between the terminologies of module & component in regard to SAP. However, for the sake of easy understanding, you may use them interchangeably.
For a comprehensive list of SAP software, visit: https://en.wikipedia.org/wiki/List_of_SAP_products
SAP NetWeaver Application Server
SAP NetWeaver Application Server – (sometimes referred to as web AS), is the interface among the SAP’s core runtime environment comprising of multiple modules and it is the technical foundation for the SAP applications, and of all the components of the SAP Business Suite. It allows organizations to integrate data, business processes, elements, and more from a variety of sources into unified SAP environments. SAP NetWeaver forms the technical foundation for a large number of SAP application landscapes.
SAP Interface
To access SAP server, either a SAPGUI or a Web Interface is provided.
- SAPGUI – a thick client application with connected SAP components on its interface. Each employee having own credentials then connects to the server he/she has been registered with.
- Web Interface – being a URL to the SAP server, SAP NetWeaver handles the HTTP interfaces of all the SAP components.
An interface to the server itself is an important attack surface that may open the door to multiple vulnerabilities.
Irrespective of which interface is being used, there could be many possible loopholes even a fully updated SAP system due to security misconfigurations. Hence, the idea is to identify, assess, and exploit the vulnerabilities that could be present in the most updated SAP systems in order to achieve Admin access to the server.
To be continued in Part 2…

Pradip bendre
Course details
Anuraag B
You can check our online courses here.