Throughout 2022 and 2023, only 0.64% of HITRUST certified organizations experienced a security breach in their certified environment!
This means getting HITRUST certification has significantly reduced the risk of a data security breach.
HITRUST has become a go-to framework for handling information security and compliance in various industries. Version 11.2 brings together 44 global standards, frameworks, and regulations to offer a holistic approach to risk management and compliance.
HITRUST assessments don’t just focus on compliance but also prioritize trust and effectiveness. By evaluating controls across different domains, HITRUST helps mitigate risks and addresses key areas such as data privacy, access management, and incident response.
However, completing the complex requirements of HITRUST, particularly in challenging domains such as password management, data protection, and access control, can be a formidable task.
This blog explores why certain controls present difficulties for healthcare organizations, the factors contributing to these challenges, the role of HITRUST assessor organizations, and actionable strategies to overcome these obstacles. But before this let’s understand about HITRUST CSF assessment and controls.
About HITRUST Assessment
The HITRUST CSF encompasses 19 distinct domains that address different aspects of the IT process. These domains are meant to be in line with various frameworks, rules, and best practices related to information security. For an organization to be deemed compliant with the HITRUST CSF, it must fulfil the control standards outlined in each domain.
A company must adhere to the control criteria within each domain. These standards outline the conditions that must be met to be deemed HITRUST CSF compliant.
For example, HITRUST’s vulnerability management emphasizes proactive identification, assessment, and mitigation of security vulnerabilities to safeguard sensitive data. It ensures organizations systematically manage risks, maintain compliance, and enhance overall cybersecurity resilience.
About HITRUST Controls
The HITRUST Common Security Framework (CSF) controls are a detailed list of security and privacy requirements created to assist organizations in handling and reducing risks related to sensitive information. The 14 control categories that make up the HITRUST CSF have unique risk factors, references, requirements, and control objectives.
Organizations can show compliance with a range of industry and regulatory standards and establish a robust security and privacy program to safeguard their sensitive data by putting the HITRUST CSF measures into place.
The Role of Control Maturity in HITRUST Certification
Achieving HITRUST certification means that organizations are following a thorough framework that covers security, privacy, and risk management standards. If a healthcare organization doesn’t fully meet HITRUST requirements or if there are issues with their control operations, there control maturity scores may be lowered.
For this, HITRUST has defined some important evaluation parameters about how well an organization’s information security policies, procedures, and controls are implemented as part of the maturity model.
To get certified, each domain must meet or exceed the certification threshold for the assessment type chosen. Here is a breakdown of the most challenging domains that HITRUST has identified for each assessment type:
Assessment Type and Lowest Scoring Domain
Assessment Type | Lowest Scoring Domain |
HITRUST r2 Validated Assessment | Password Management |
HITRUST i1 Validated Assessment | Data Protection & Privacy |
HITRUST e1 Validated Assessment | Access Control |
Why Are These Domains Difficult to Maintain?
Healthcare organizations face unique challenges in maintaining the maturity of these domains due to several factors, including complex regulatory requirements, legacy systems, and resource constraints. Below, we examine each domain in detail.
Password Management: Complexity in Large-Scale Environments
In HITRUST r2 assessments, password management often scores low due to:
- Human Factors: Healthcare employees frequently reuse passwords or choose weak passwords due to the pressure of managing multiple systems. For instance, clinical staff may use simple passwords to quickly access electronic health records (EHRs) during emergencies.
- Lack of Centralized Controls: Many healthcare organizations rely on fragmented identity and access management systems, making it difficult to enforce enterprise-wide password policies.
- Legacy Systems: Older healthcare systems often lack compatibility with modern password management tools, hindering the adoption of strong authentication practices.
Solution: Implement multi-factor authentication (MFA) across all systems, enforce strong password policies, and deploy enterprise-level password managers to streamline credential security.
Data Protection & Privacy: Balancing Accessibility with Security
Data protection and privacy are particularly challenging for HITRUST i1 certification due to:
- High Volume of Sensitive Data: Healthcare organizations handle vast amounts of protected health information (PHI), making data encryption and monitoring complex.
- Interoperability Requirements: The need for seamless data exchange between healthcare providers, insurers, and third-party vendors often leads to security vulnerabilities.
- Evolving Regulatory Landscape: Compliance with HIPAA, GDPR, and other regulations demands constant updates to privacy policies and practices.
Example: A hospital’s failure to encrypt PHI in transit led to unauthorized access during data exchange with an external laboratory, resulting in a breach and regulatory penalties.
Solution: Implement robust encryption for data at rest and in transit, conduct regular privacy impact assessments, and establish clear governance for third-party data access.
Access Control: Managing Privileged Access in Dynamic Environments
Access control presents challenges for HITRUST e1 certification due to:
- Role Complexity: Healthcare roles often overlap, making it difficult to enforce role-based access control (RBAC). For example, a physician may require access to multiple systems but only for specific functions.
- Frequent Staff Turnover: High turnover rates in healthcare complicate access revocation processes, increasing the risk of insider threats.
- Limited Monitoring: Many healthcare organizations lack real-time monitoring tools to track access anomalies, such as unauthorized attempts to view patient records.
Solution: Adopt privileged access management (PAM) solutions, implement real-time access monitoring, and conduct periodic audits to ensure access rights align with job functions.
Why do HITRUST Certification Matters for Healthcare?
Achieving HITRUST certification offers healthcare organizations numerous benefits:
- Enhanced Risk Management: Strengthens defenses against data breaches and ransomware attacks.
- Regulatory Compliance: Simplifies adherence to HIPAA, HITECH, and other mandates.
- Patient Trust: Demonstrates a commitment to protecting sensitive patient information.
Simplify Healthcare Compliance with Network Intelligence!
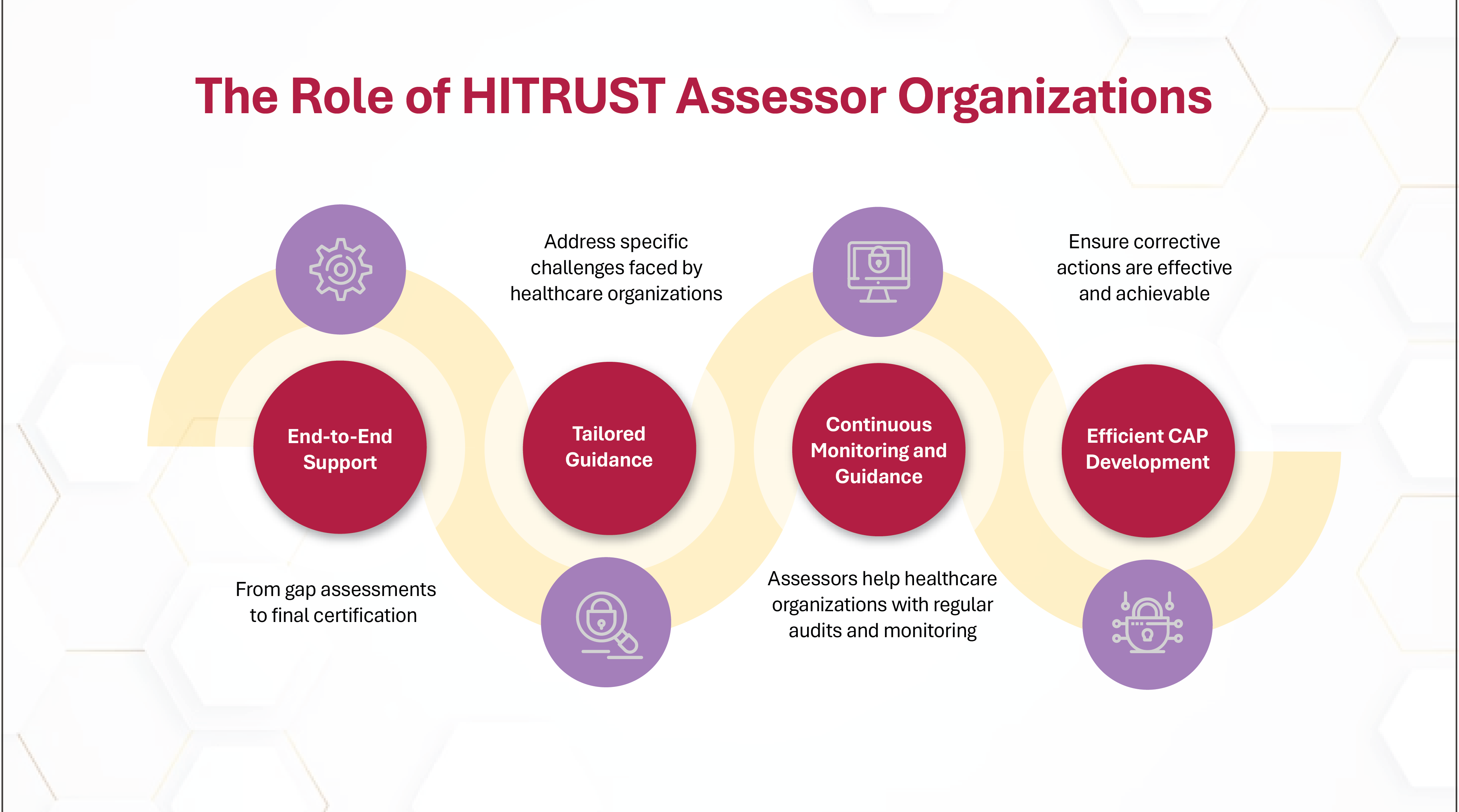
By leveraging the expertise of HITRUST assessor organizations like Network Intelligence, your organization can achieve certification while building a robust cybersecurity foundation.
We offer continuous guidance in adopting emerging technologies, adapting to evolving regulations, and strengthening control maturity. This forward-thinking approach ensures resilience against cybersecurity threats while maintaining trust and compliance.
Take the next step towards HITRUST certification. Connect with our experts who will help ensure your organization successfully meets HITRUST requirements.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
