
Reverse Engineering x64 for Beginners – Linux
Prologue The main focus of this blog is to give a push start to the beginners to get in the field of reverse engineering. Since […]

Prologue The main focus of this blog is to give a push start to the beginners to get in the field of reverse engineering. Since […]

Welcome to the part 4 of malware development .In the previous parts 1, 2-1, 2-2 and 3, we created a binary which can listen to […]

In the previous parts 1, 2-1 and 2-2 of this series we created a binary that can connect to, and parse commands sent via netcat […]

In the previous parts of this blog series, I introduced the concept of writing a full-undetectable malware and about writing a client-side socket using […]

Welcome to the second part of the malware development blog series. Here’s the link to Part 1. Given the length of Part 2, I have […]

If you are in cybersecurity, especially Red Teaming, writing a full-undetectable (FUD) malware is a great skill to have. Folks tend to use Metasploit combined […]
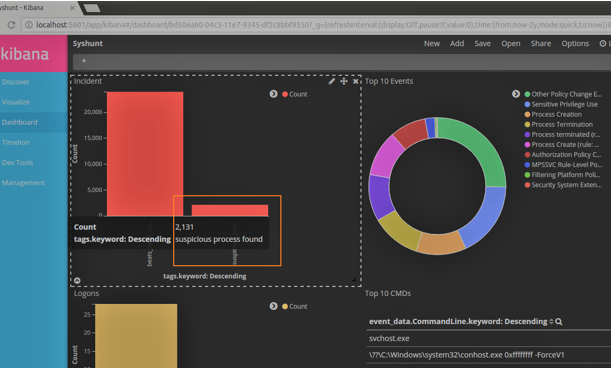
An important aspect of effective threat hunting is to understand what is normal in an environment. If a threat hunter is able to baseline the […]
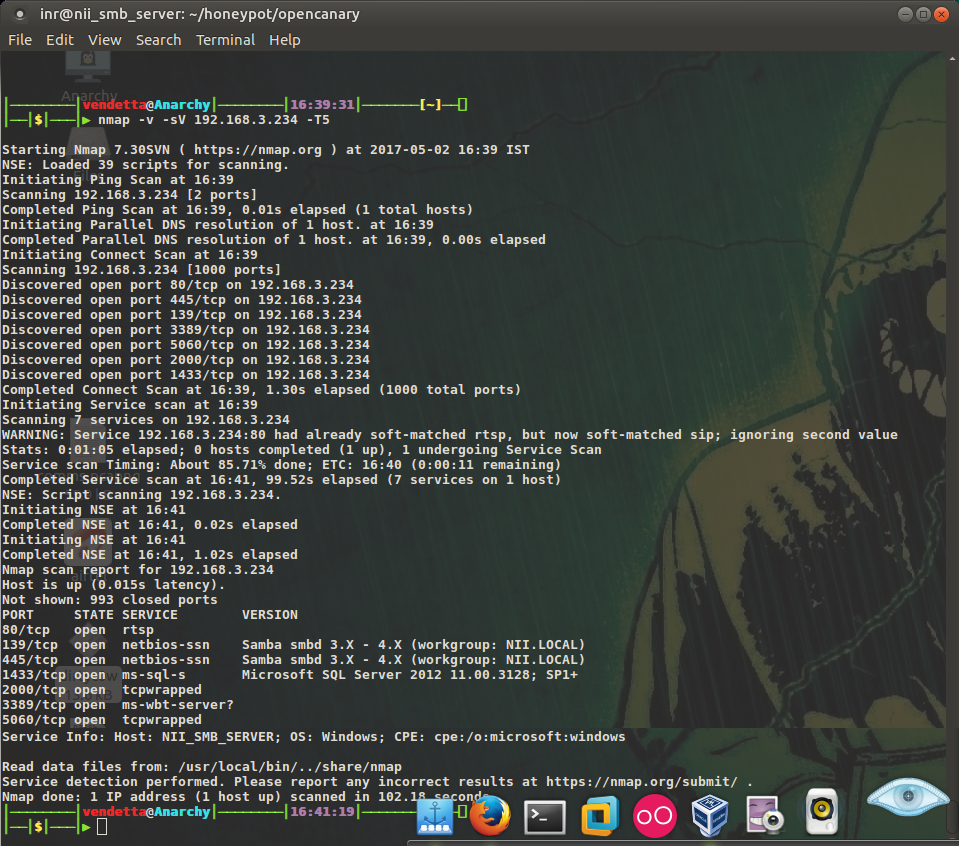
Before we start to configure our decoys and put it in our production environment, let’s take a look at what exactly it is and how […]
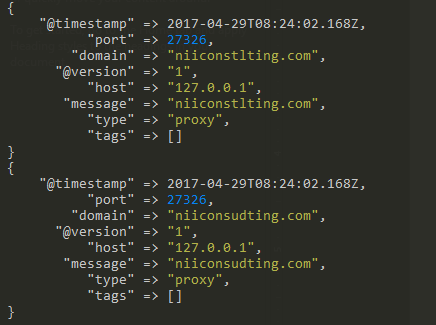
Most organizations face a barrage of attacks every day from threat actors around the globe. Among the various vectors, attackers have found relatively high degree […]
Introduction When an attacker compromises an end-point system in an organization, he needs some sort of confirmation that: his code was executed on the targeted […]