
Preventing Data Breaches: How MSSPs Can Protect Your Business?
As businesses increasingly rely on digital infrastructure, the specter of data breaches looms larger than ever. According to IBM’s report, […]

As businesses increasingly rely on digital infrastructure, the specter of data breaches looms larger than ever. According to IBM’s report, […]

One of the most critical factors that determine the success and efficacy of a digital forensic investigation is putting together […]

Introduction With each passing day, the world is waking up to new global cybersecurity challenges. The latest one was unearthed […]

Note: This is a technical deep-dive into DearCry ransomware. If you want a preliminary analysis of the ransomware, you can […]

Note: We have also done a technical analysis on DearCry. Read here. It’s a warm summer morning. While sipping your […]

Data exfiltration is a common data theft technique and most feared cyber-attack. it is a data breach that happens when […]
Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. […]
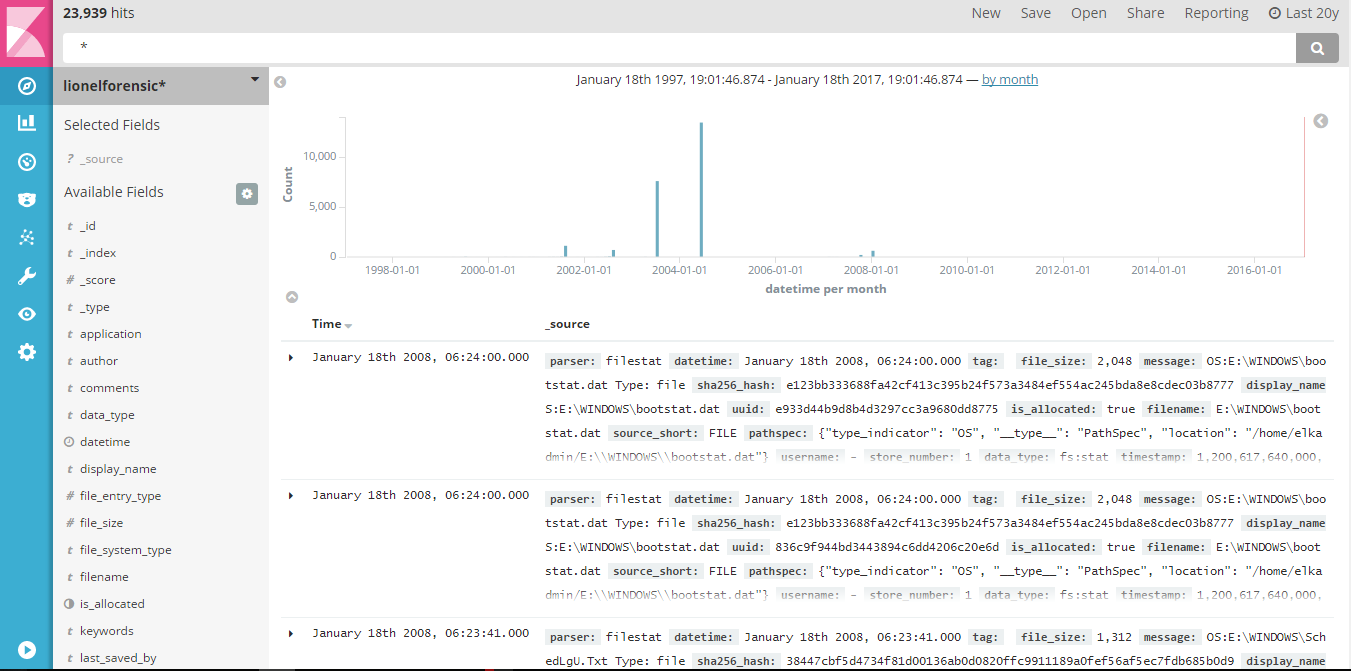
ELK Stack is a collection of three components – Elasticsearch, Logstash & Kibana Logstash – This component is responsible […]
INTRODUCTION Point-of-sale (POS) is the place where a retail transaction is completed. It is the point at which a customer […]
Introduction Android is an open source operating system based on the Linux kernel, initially developed by Android Inc., which Google […]