Security Analytics Using ELK
Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. […]

Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. […]
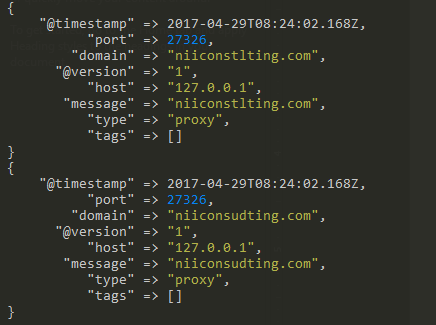
Most organizations face a barrage of attacks every day from threat actors around the globe. Among the various vectors, attackers […]
Introduction When an attacker compromises an end-point system in an organization, he needs some sort of confirmation that: his code […]
The Payment Card Industry Security Standards Council recently released their updated Information Supplement: Penetration Testing Guidance. The guidance document was […]
During a recent engagement, we were asked to test the security level of an application white-listing solution deployed on the […]
Most large organizations provide wireless facilities for their guest, which may include vendors, consultants, business associates, employees from other regions […]
Below are the steps of how to fix the banner (version information) in IIS 7.5 Install the latest version of […]
With the boundary-less work culture of the 21st century, organizations have started to wake up to the fact that they […]
Hi all, This month’s reading list. Make sure to check out the tools sections. Traditional Pen-testing is Dead: A frank look […]
Hi all, We are starting with a monthly reading-list for people who are unable to keep up with the latest […]