
Malware Development – Welcome to the Dark Side: Part 2-1
Welcome to the second part of the malware development blog series. Here’s the link to Part 1. Given the length of Part 2, I have […]

Welcome to the second part of the malware development blog series. Here’s the link to Part 1. Given the length of Part 2, I have […]

If you are in cybersecurity, especially Red Teaming, writing a full-undetectable (FUD) malware is a great skill to have. Folks tend to use Metasploit combined […]
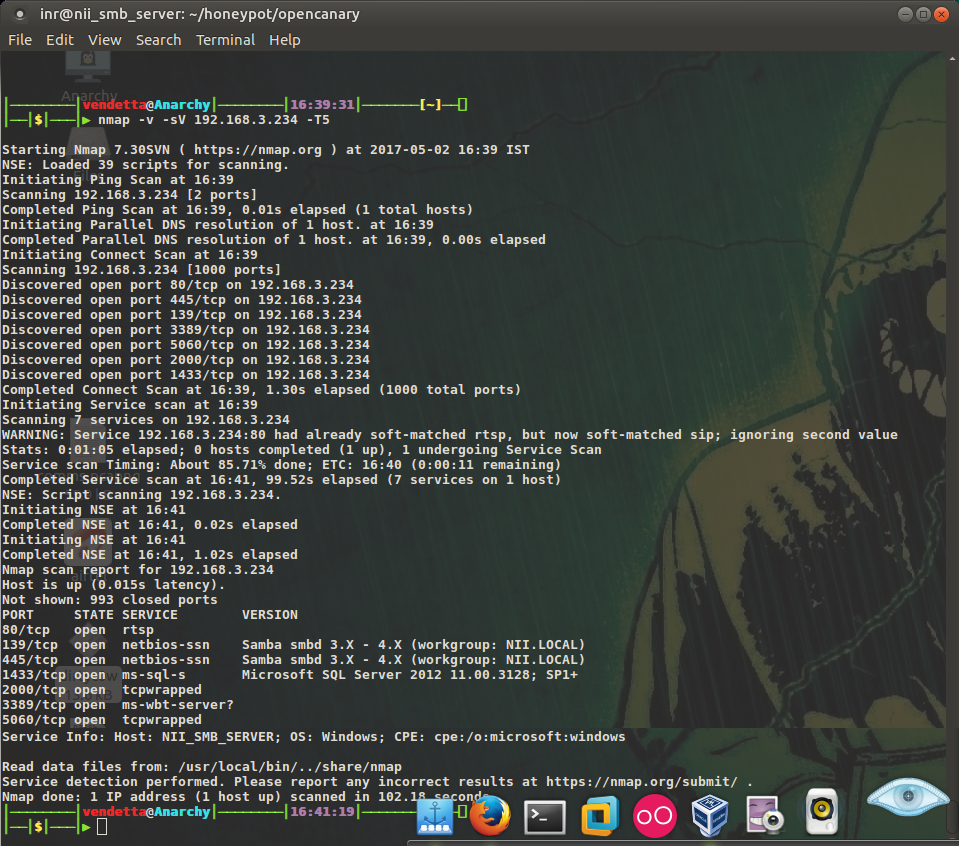
Before we start to configure our decoys and put it in our production environment, let’s take a look at what exactly it is and how […]
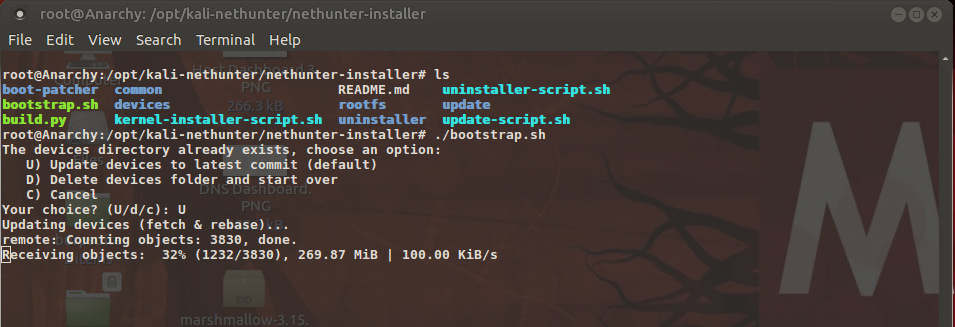
Part IV: Customizations – Custom Kernels and building Chroots This is the blog part 4 of building your custom Pentesting device. If you haven’t read […]
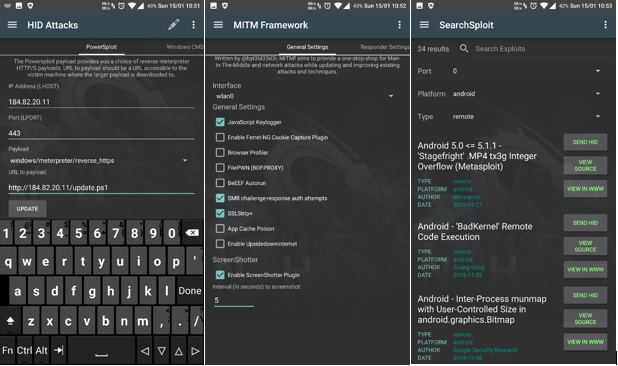
Part III: Cracking the Lid – Rooting and Unlocking Bootloaders This is part 3 of building your own mobile pen-testing device. Here’s the link to […]
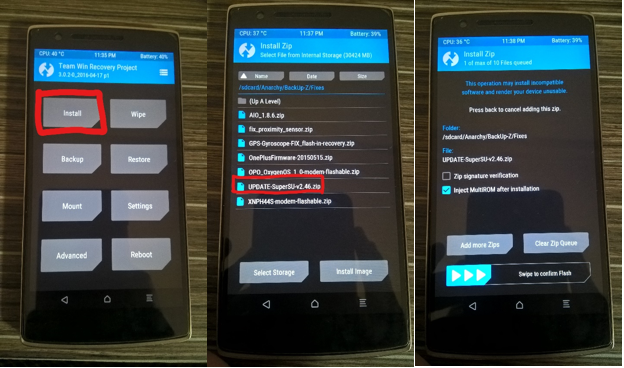
Part II: The Technicalities – Linux Kernels and chroots This is part 2 of building your own mobile pen-testing device. Here’s the link to part […]
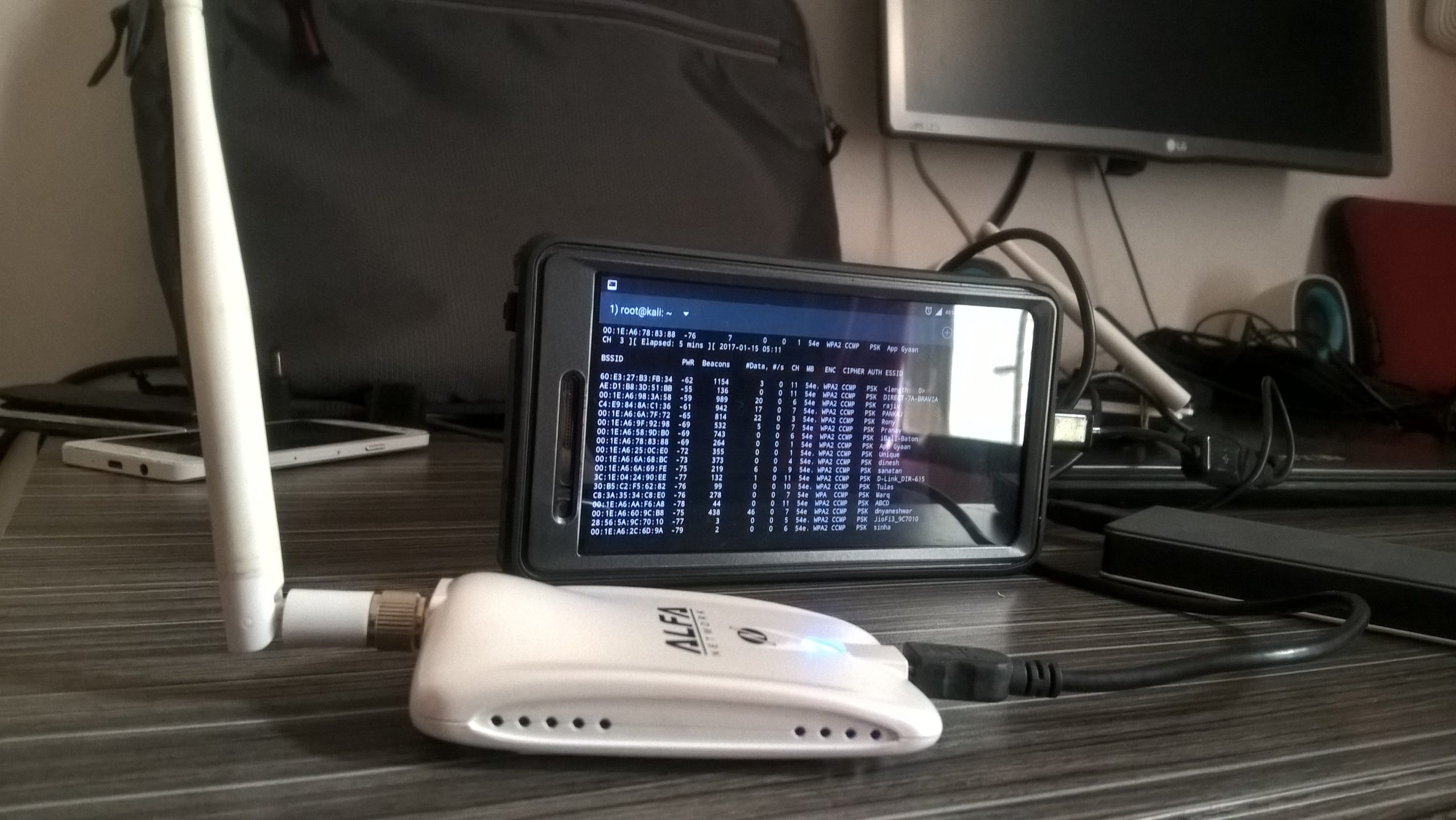
Part I: The Prologue – Android rooting Background In the game, Watchdogs, the hacker ‘Aiden Pierce’ uses his cell phone alone to hack into organizations […]